Introduction
In this post, we will walk through the Cisco ISE posture remediation configuration to automatically remediate the endpoint before giving network access.
What does device posture mean? Device posture is a feature that provides the health of an endpoint, it ensures the endpoint that meets the compliance is allowed to get network access and the devices which doesn’t meet the compliance are not allowed to get network access. If the endpoint doesn’t meet the compliance, it needs to be remediated to meet the compliance and allow for network access. Cisco ISE remediation can perform automatic remediation. A real-world example of the posture assessment is that we need to ensure devices are allowed for network access only when they are running an Endpoint detection and response (EDR) agent on the system.
To perform the posture assessment a posture agent needs to run on the endpoint which then further sends the posture state to the Cisco Identity services engine. Posture state can be either compliant or non-compliant or unknown. When the posture agent provides the non-compliant status of the endpoint that’s when remediation is needed. The posture agent also needs a compliance module that helps in accessing the posture status of the endpoint. We need to ensure the latest compliance module is been used on the ISE.
Table of Contents
Posture Remediation – Options
Remediation options are available for the following checks on Cisco ISE:
- Anti-Malware
- Anti-Spyware
- Anti-Virus
- Application
- File
- Firewall
- Launch Program
- Link
- Patch Management
- Script
- Windows Server Update Services Remediations
- Windows Update
- USB
Refer to the previous post on the blog for complete Cisco ISE posture configuration. In this post, we will only focus on automatic remediation configuration. Check the Cisco ISE configuration guide on the Cisco website for more details.
ISE Posture Remediation – Steps
The configuration involves 7 steps. For this post, we will focus on steps 3 and 4. The rest of the configuration is available in the previous post.
Note: All the Cisco ISE posture configurations remain the same except under the requirement for Cisco ISE remediation we have to select the automatic remediation option we will learn how to configure it in this post.
1> Define posture condition.
2> Create Requirements.
3> Create Remediation configuration
4> Create a posture policy.
5> Create a client provisioning policy.
6> Create authorization profile and authorization profile.
7> Endpoint 802.1x configuration and agent installation on endpoint.
Cisco ISE posture Remediation – Remediation Config
Create a remediation action:
Under the remediation policy, we can select the remediation type as automatic or manual.
Navigate to Policy > Policy Elements > Results > Remediation Actions – Select Firewall, Click Add. For this post, we are configuring a firewall remediation for Windows machines.
If the Windows firewall is disabled, The agent will enable the firewall with automatic remediation.
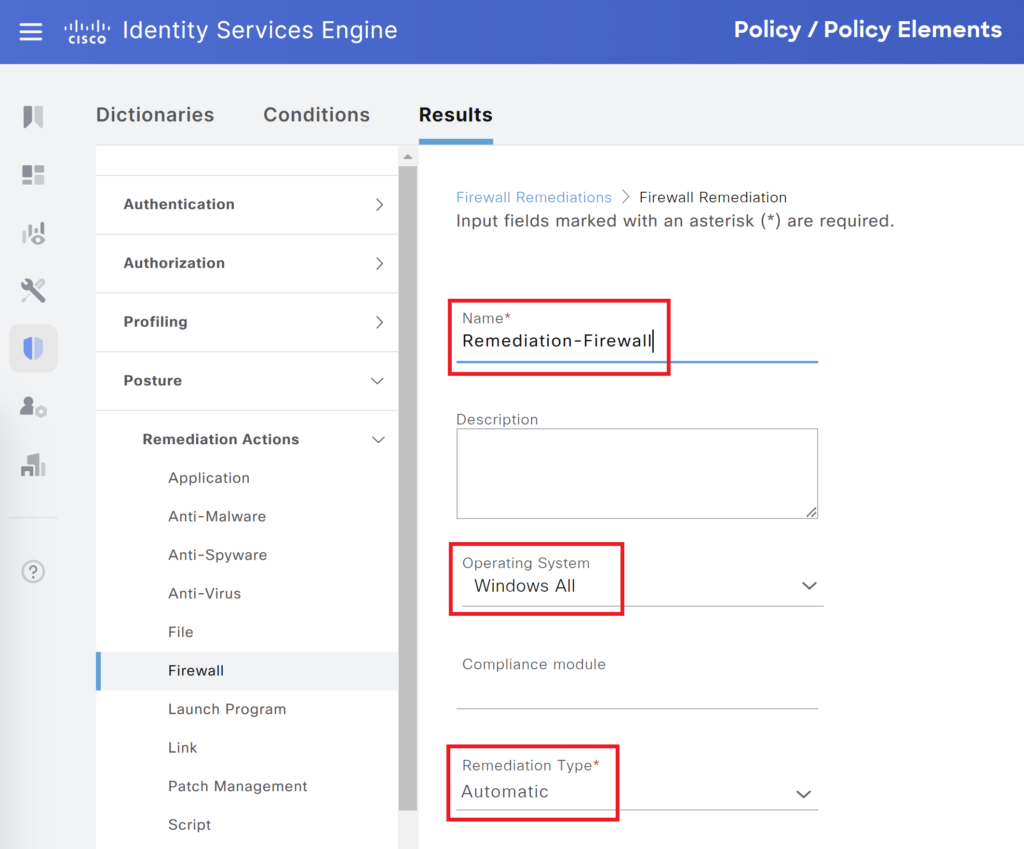
Select the appropriate vendor, version.

Cisco ISE posture Remediation – Requirement
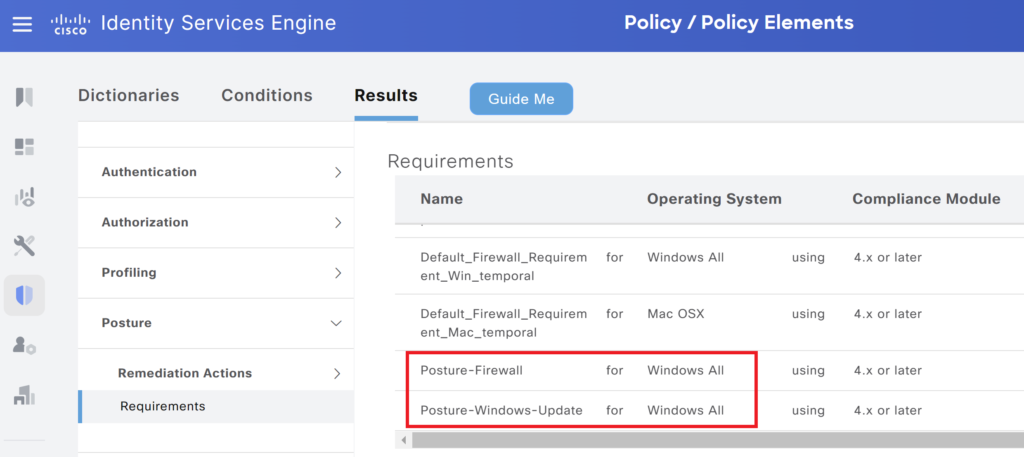
Create a Requirement: Under the requirement, we have to specify the name of the requirement, operating systems, the condition we want to apply, and the respective remediation action.
Navigate to Policy > Policy Elements > Result > Posture > Requirements – Scroll to the right and click the down arrow to select Insert New Requirement. You can choose the action created in previous steps from the list of remediation actions. One of the options for remediation is to configure a message text only, which will result in a pop-up message for the user.
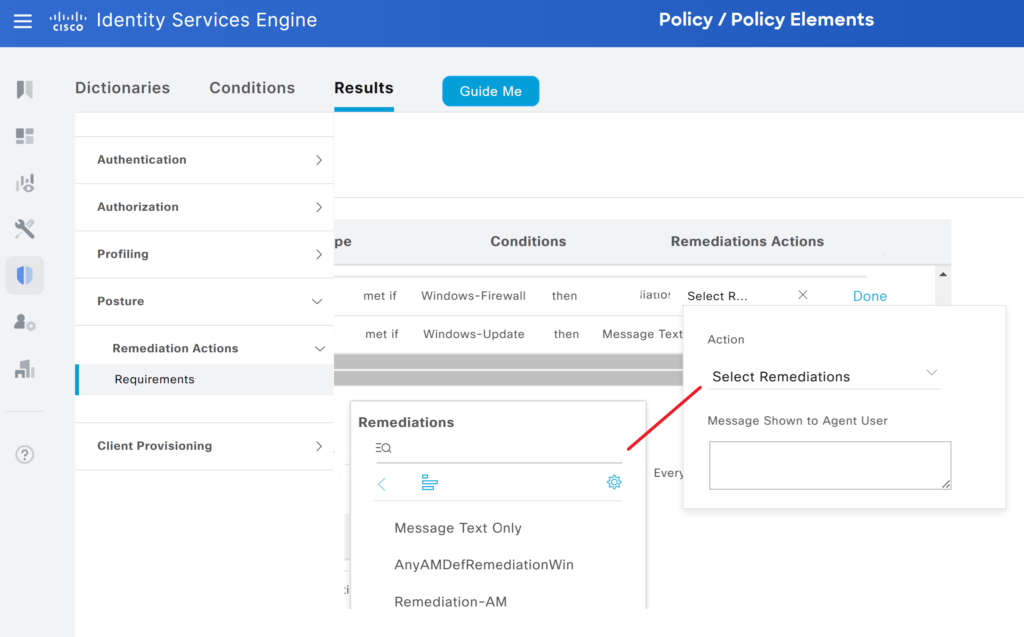
In this example we are using automatic remediation for firewall conditions and Message Text for Windows updates.
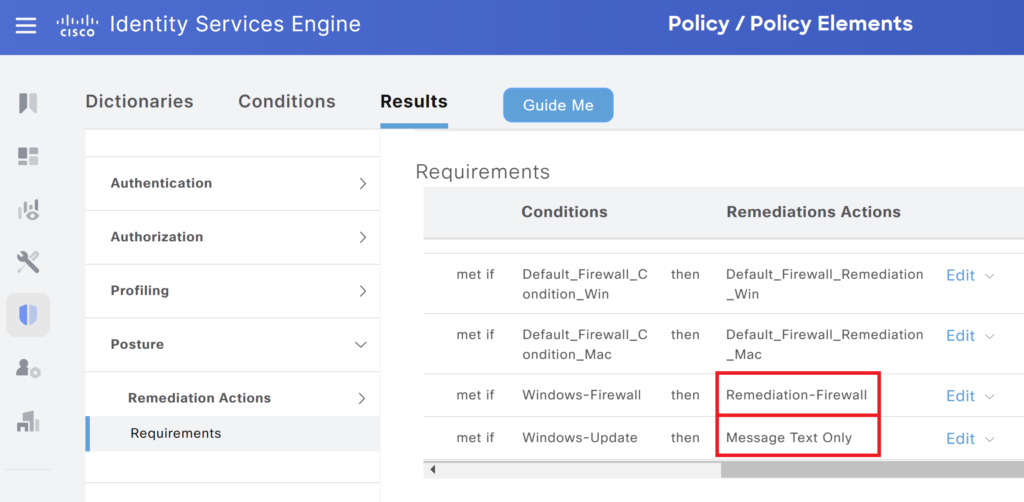
Note: The rest of the steps are the same as in the post for Cisco ISE Posture Configuration.
Now with the Cisco ISE posture remediation configuration in place when the endpoint has a Windows firewall in a disabled state, the Posture agent automatically enables the firewall. This reduces user overhead and the amount of work an administration needs to do when the endpoints are non-compliant.
Check our post on how to integrate Cisco ISE with other Cisco security products using the pxgrid 2.0 protocol.
So, what are your thoughts on Cisco ISE Remediation? Have any questions? Let us know in the comments.