In this post, we will walk through the step-by-step configuration of Cisco FTD AnyConnect Azure SAML based authentication. There are 7 steps involved in the entire configuration. Cisco AnyConnect has been renamed to Cisco Secure Client. The SAML-based integration remains the same for other SAML providers like Cisco DUO, Okta, etc.
Cisco FTD AnyConnect Azure SAML – Azure configuration
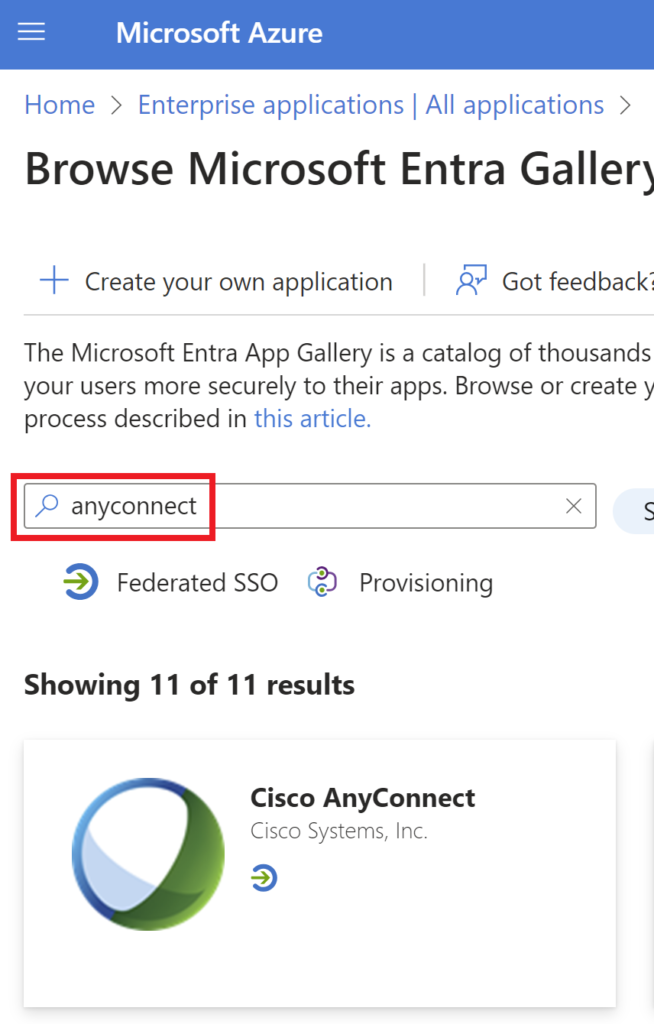
Step 1> Under Microsoft Azure create an Enterprise Application. Search for Cisco Anyconnect.
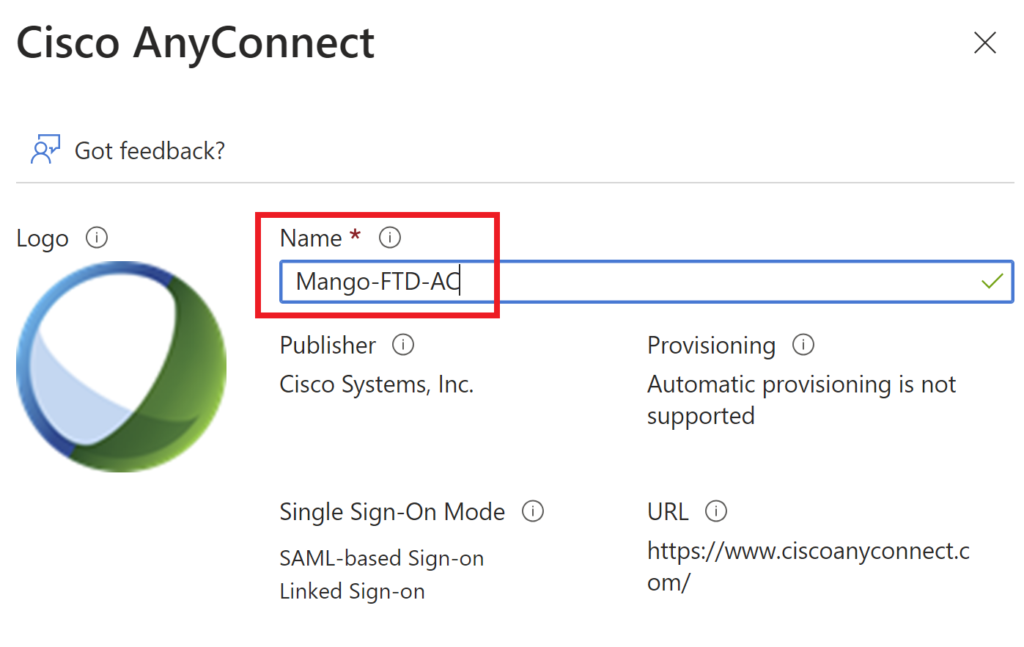
Give a Name to the application.
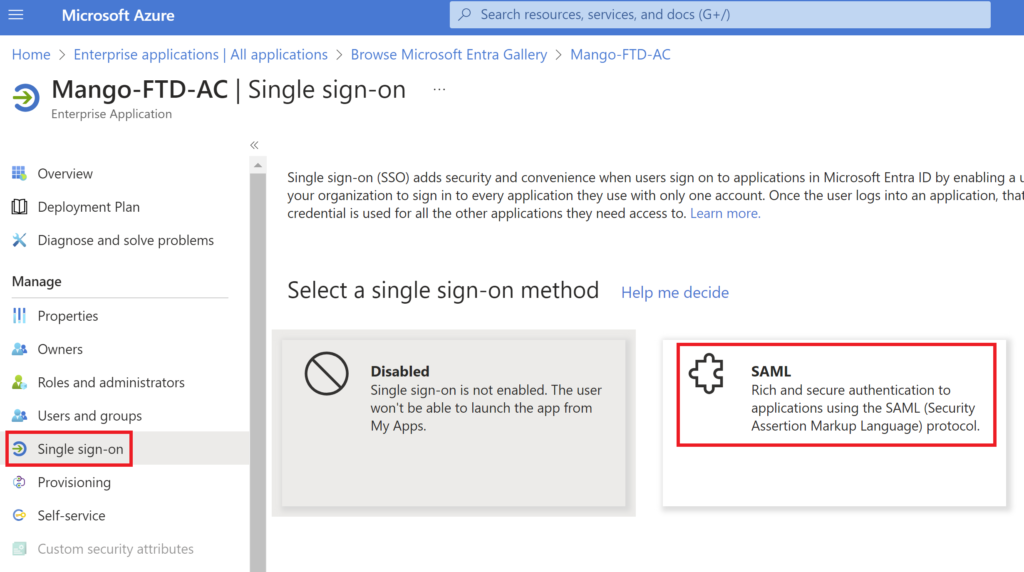
Under the Single sign-on tab select SAML method.
Edit the configuration and provide the details.
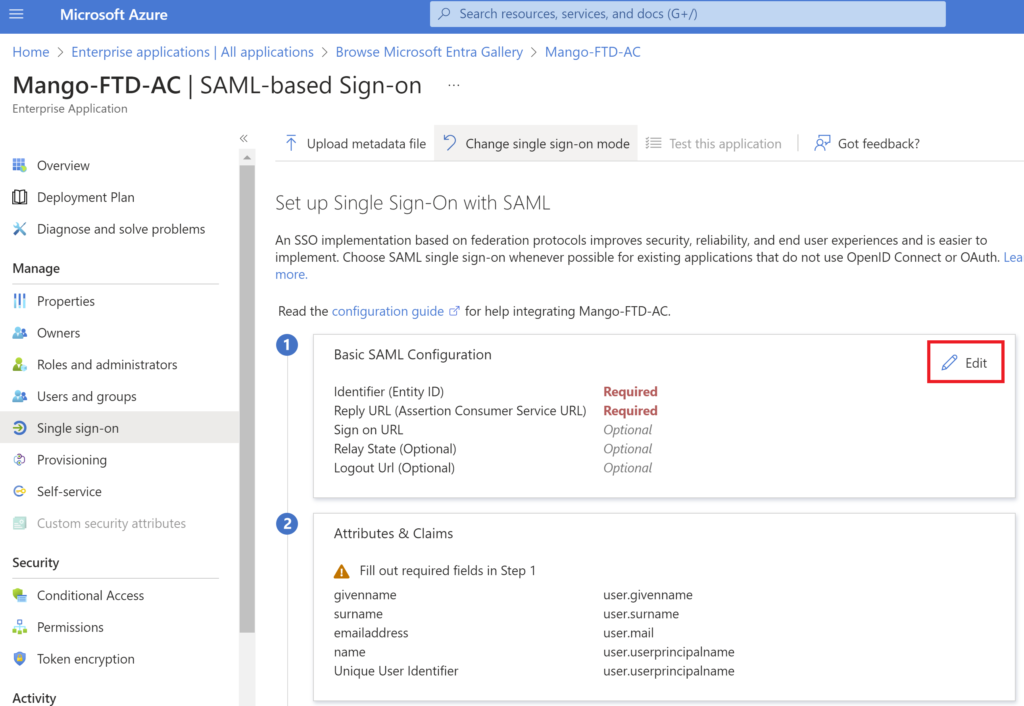
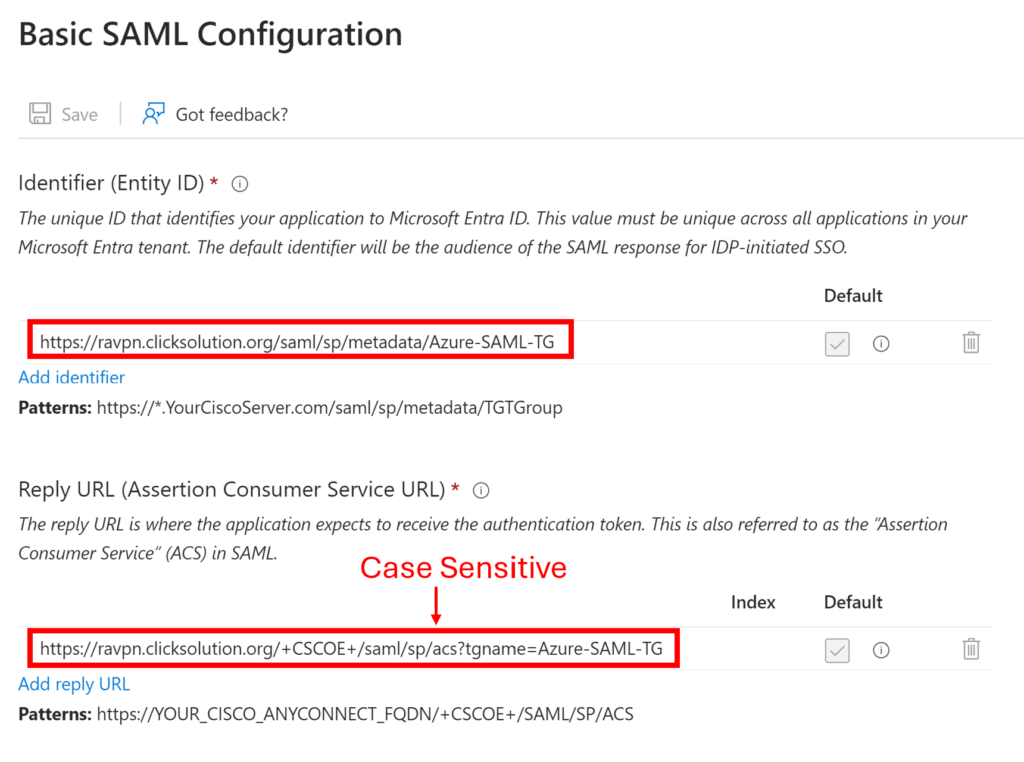
Enter Entity ID ensure in the format https://<FQDN>/saml/sp/metadata/Azure-SAML-TG
Enter Reply URL as well in the format given in the screenshot. Note the reply URL is case sensitive.
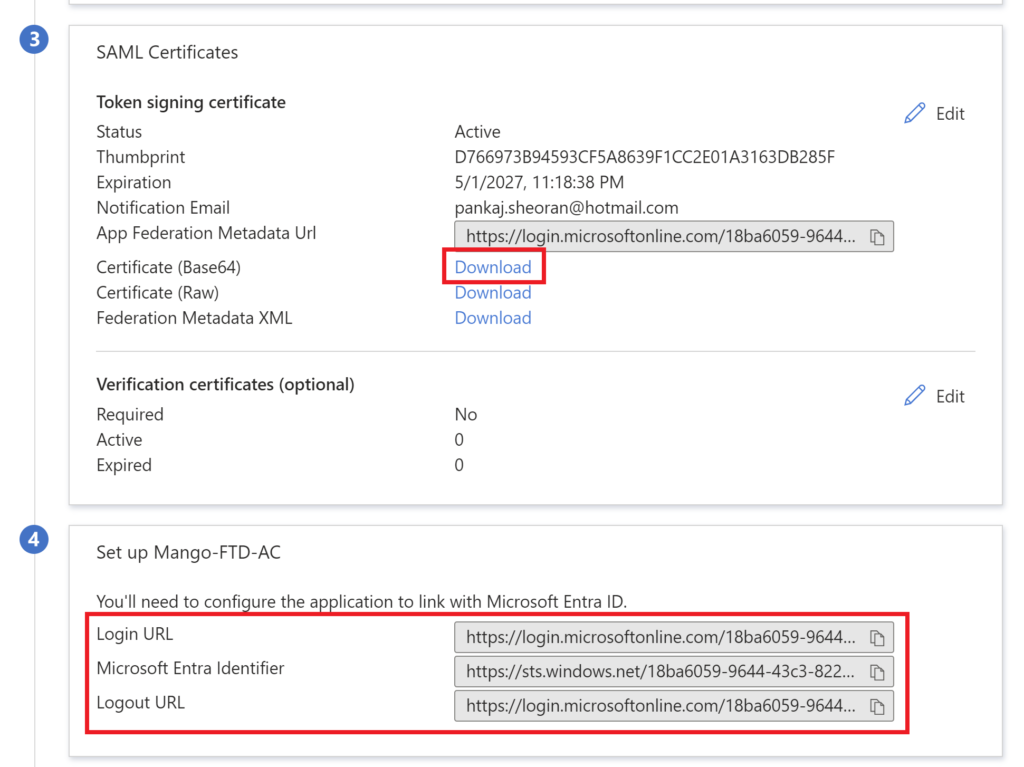
Download the SAML certificate; it’s required during FTD configuration. Copy Login URL, Microsoft Entra Identifier, Logout URL.
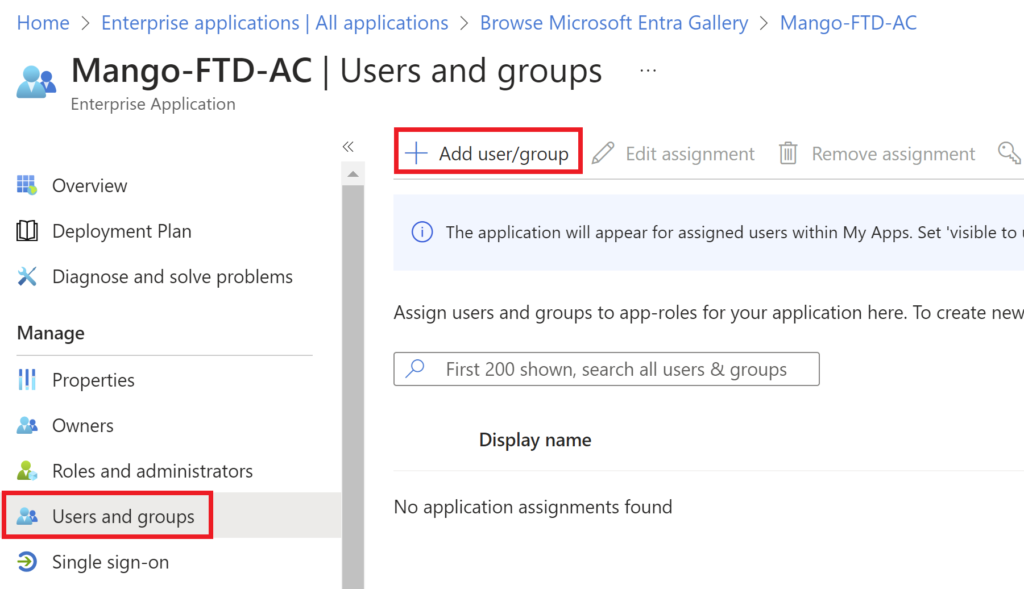
Add the users allowed to access the remote access VPN.
Cisco FTD AnyConnect Azure SAML – FTD configuration
Import the SAML certificate exported in previous step.
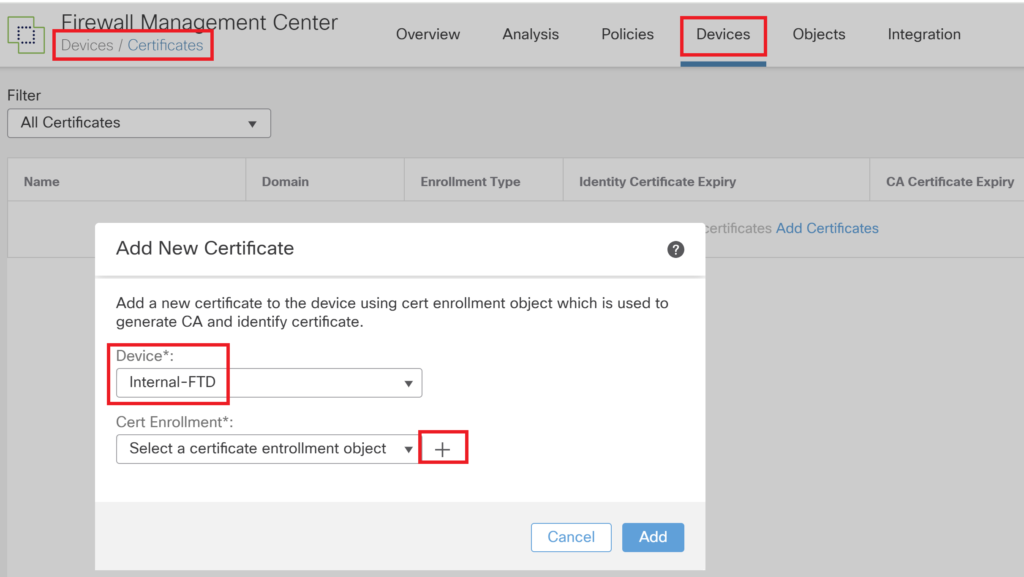
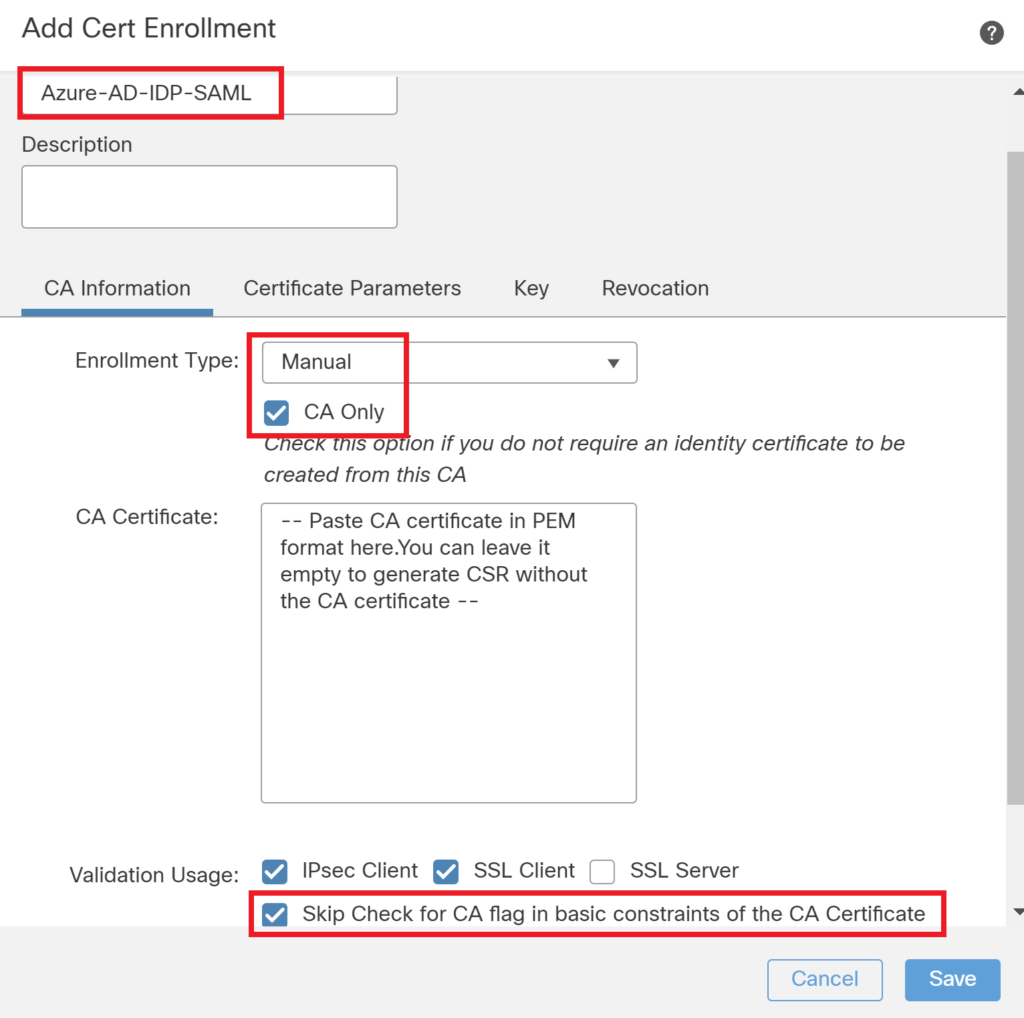
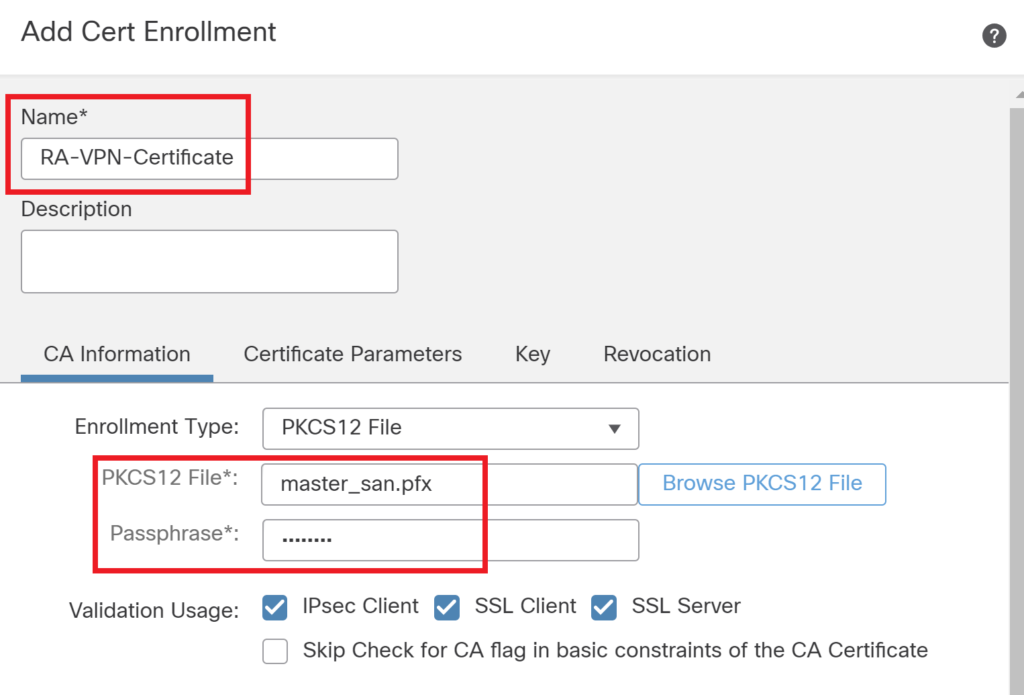
Get one external CA signed certificate for RA VPN. Internal CA signed certificate may also work however if the endpoint doesn’t have internal CA into trust store certificate warning would not allow the connection establishment.
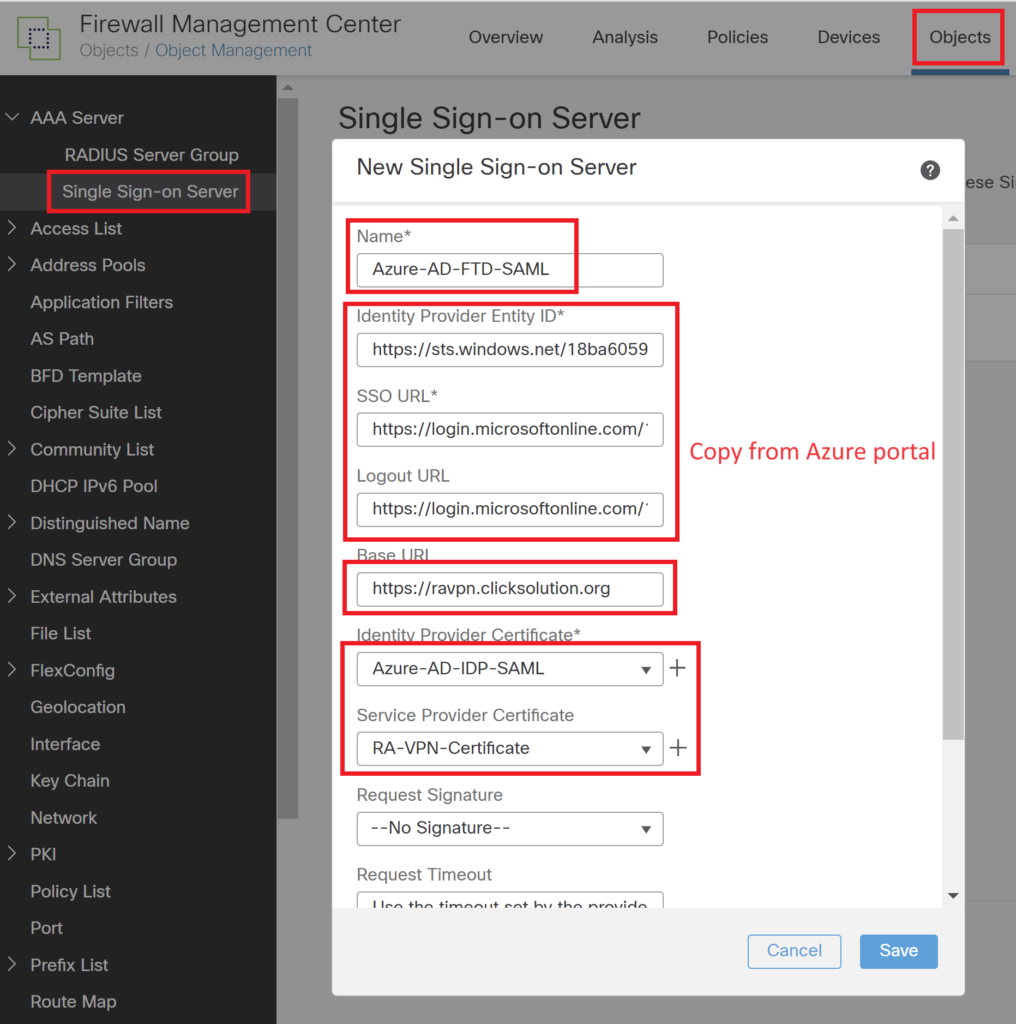
Create a Single Sign-on Server and enter the details from the previous step. Select the certificate imported in the last steps.
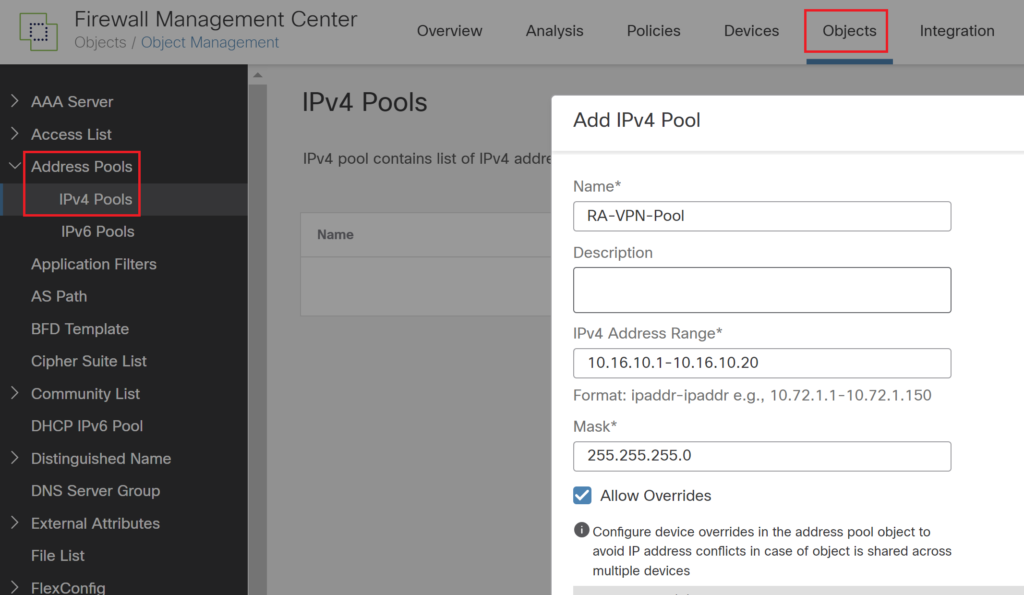
Define an Address Pool, Remote access VPN users will get an IP address from this pool.
Create a group policy, specify
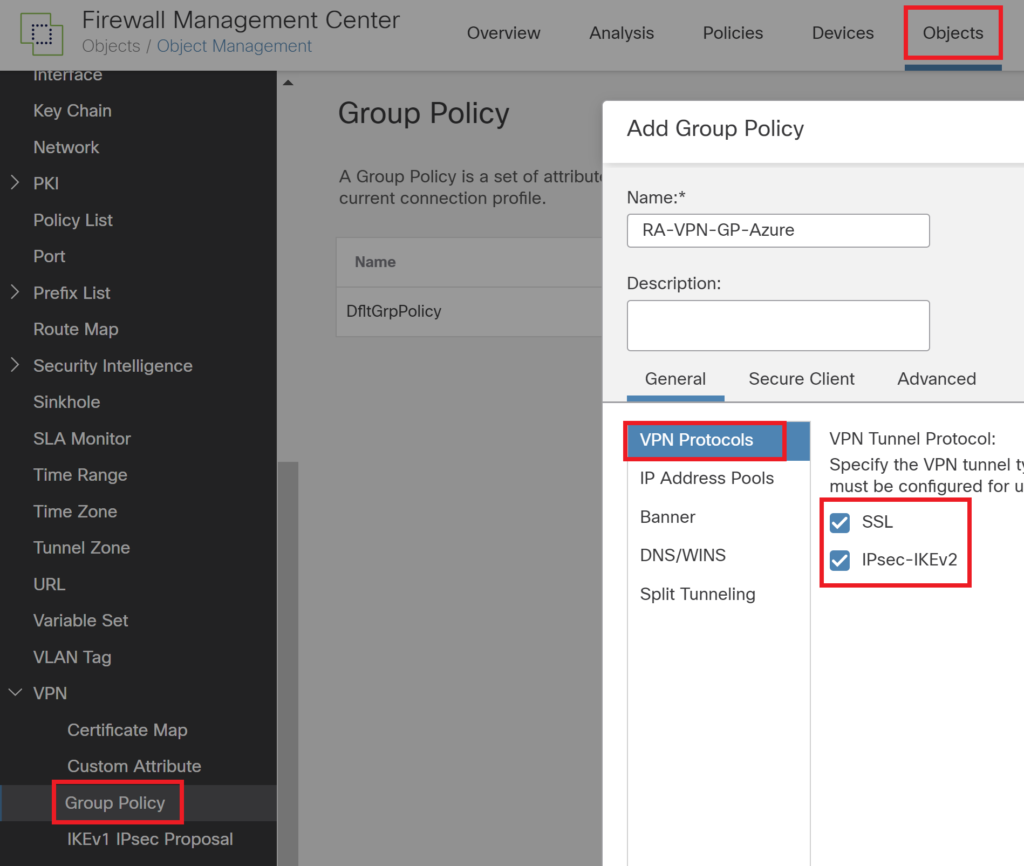
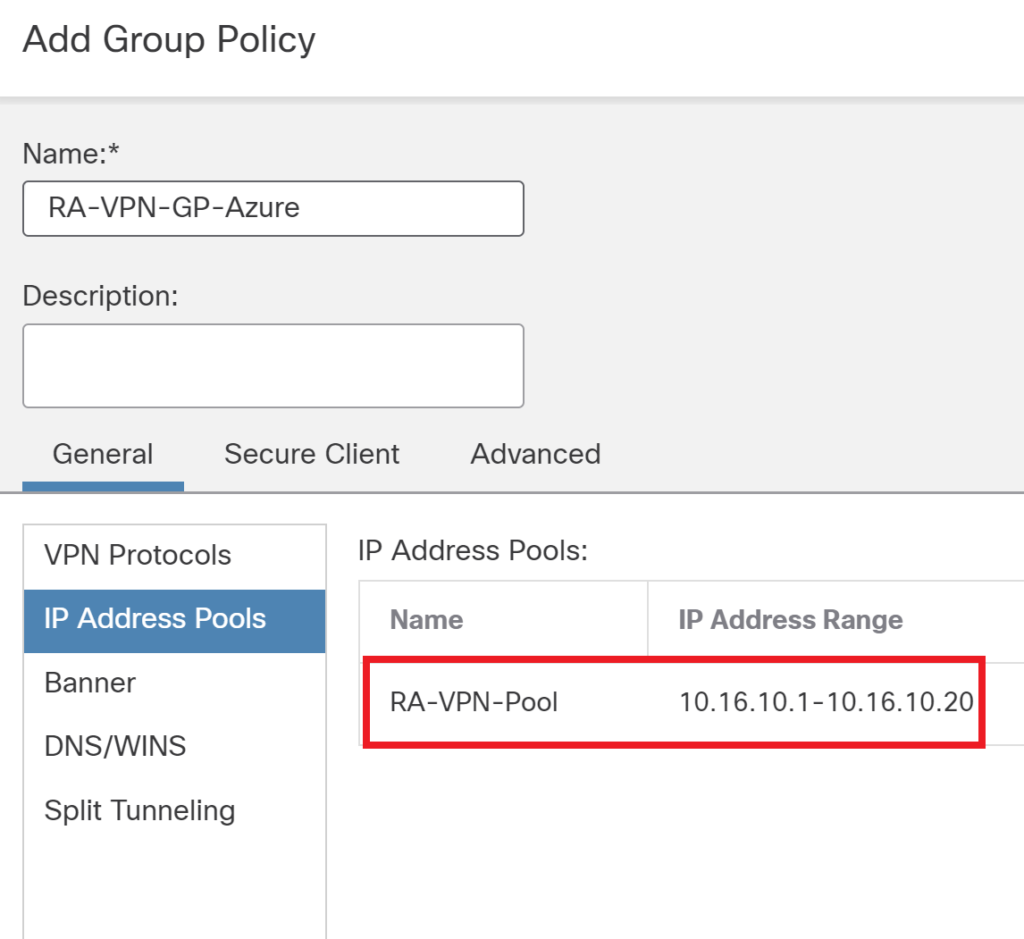
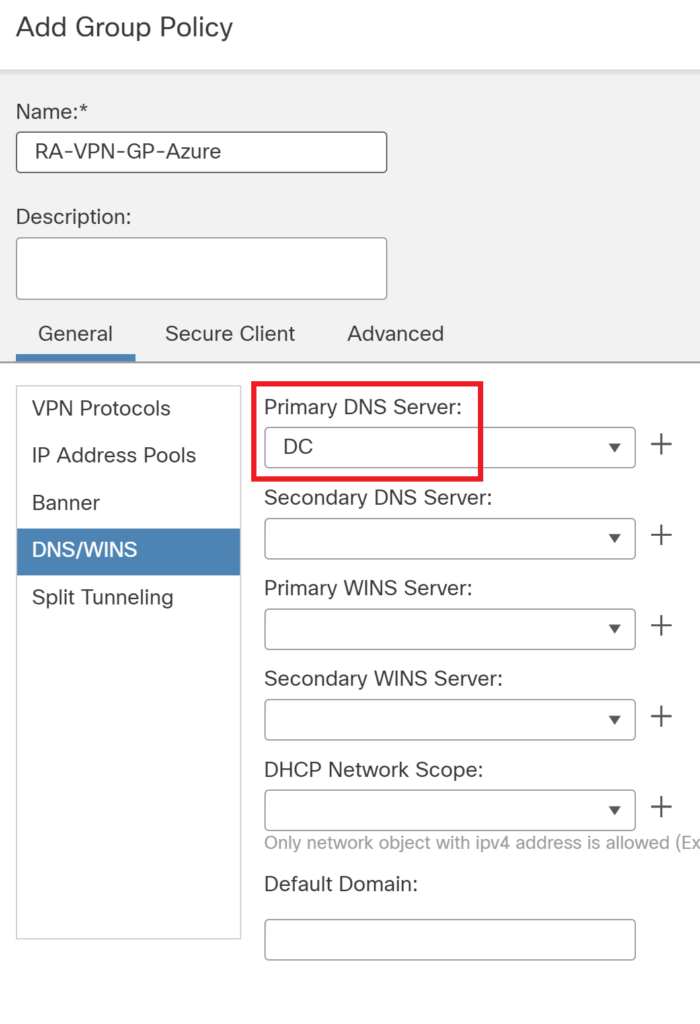
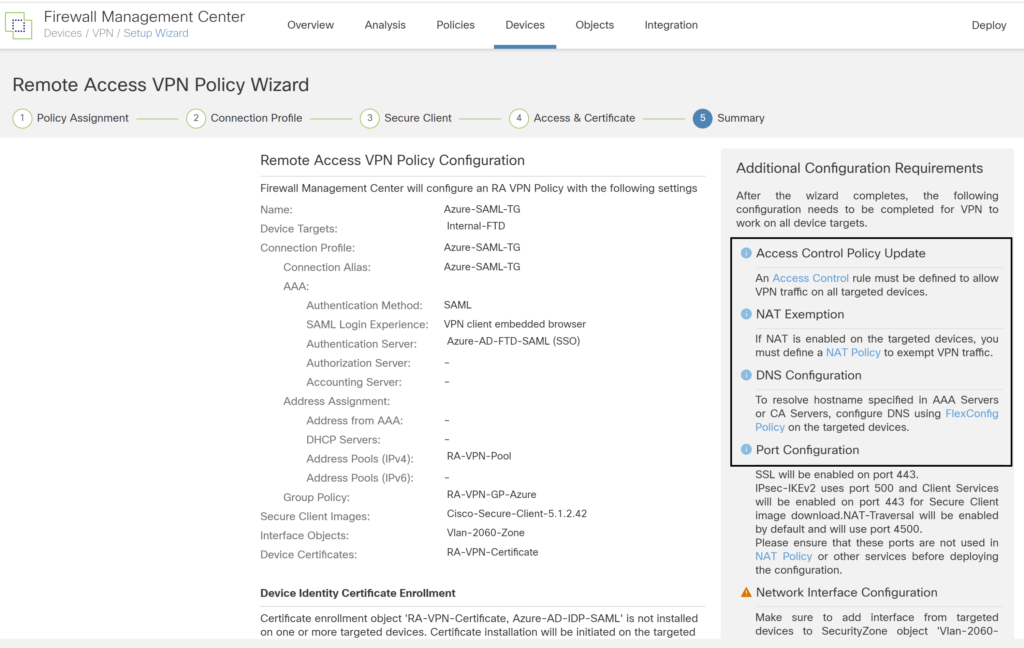
Navigate to Devices > VPN > Remote access VPN and set up remote access VPN configuration. Follow the wizard. Ensure the name in the steps matches the name in the Azure portal.
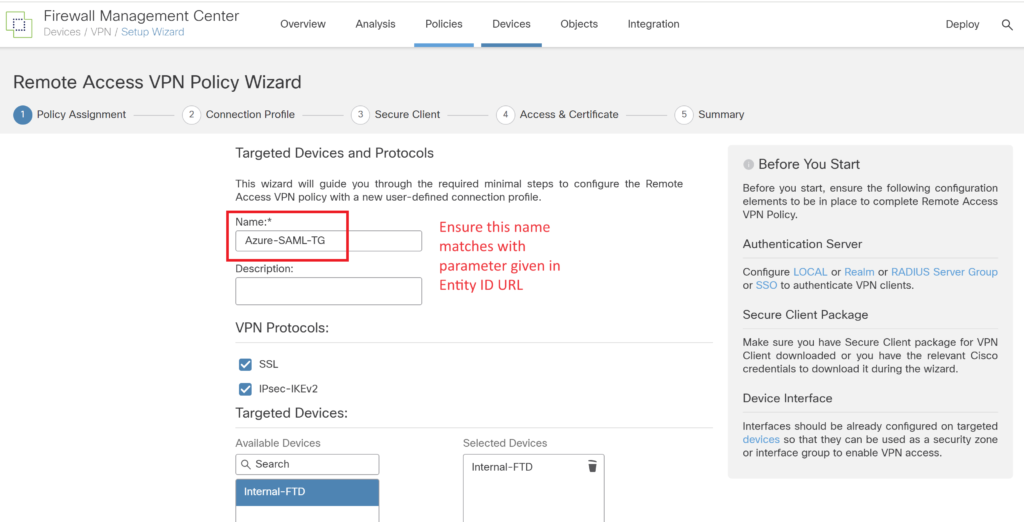
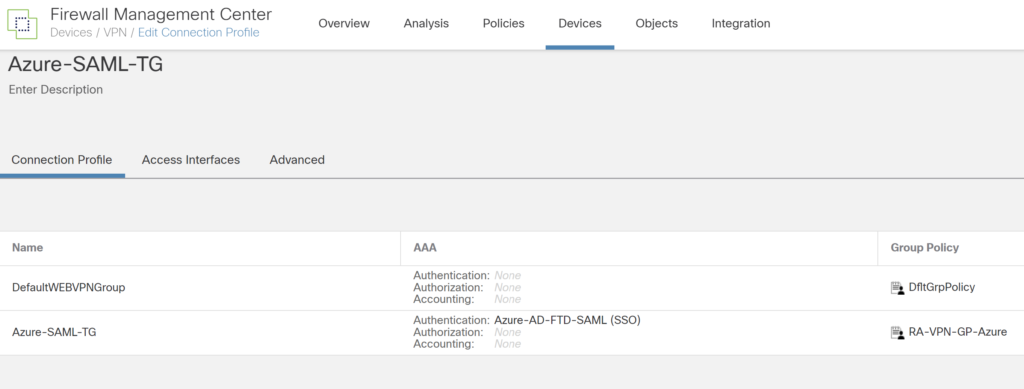
Select the method as SAML and under authentication server select the SAML profile created earlier.
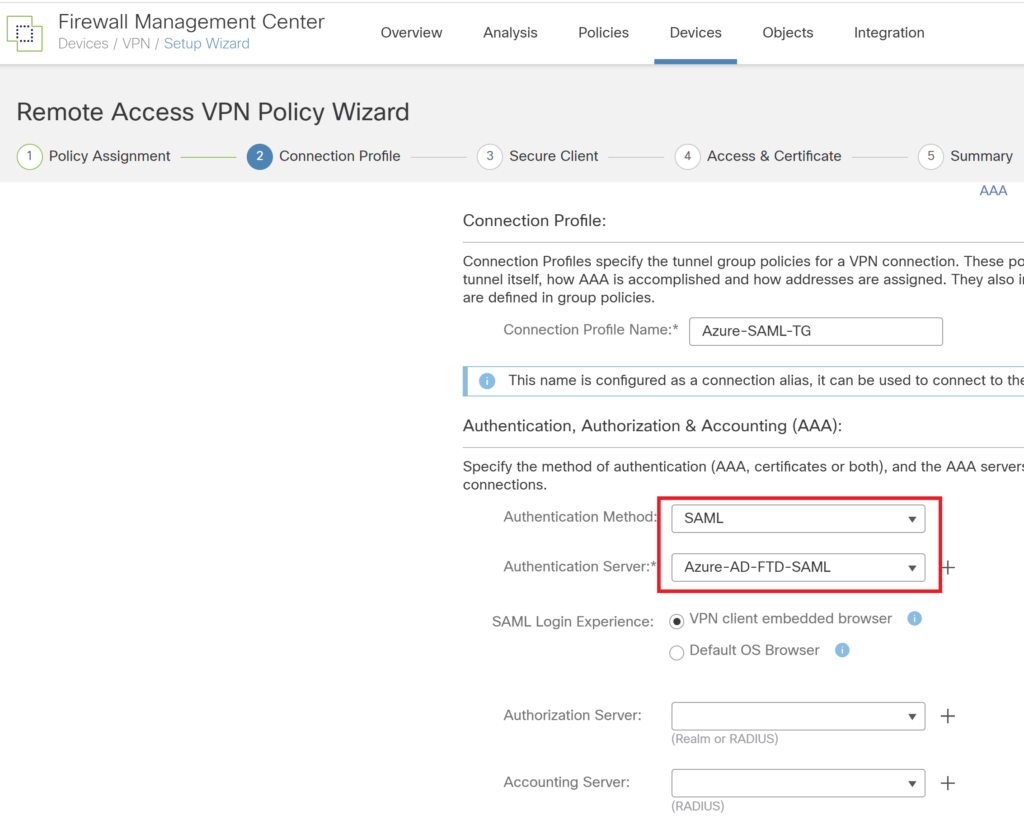
Select the address pool and the group policy created in earlier step.
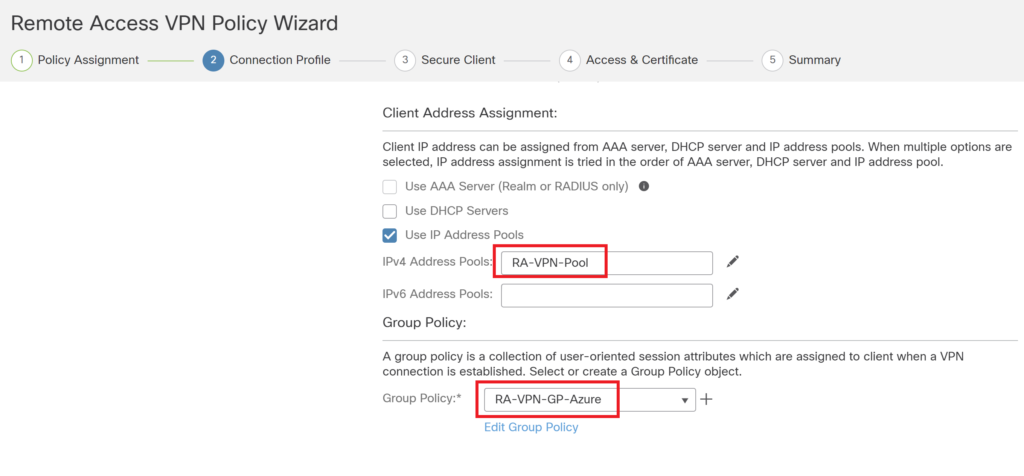
Download the Cisco AnyConnect (Cisco Secure client) package from the Cisco website and upload it.
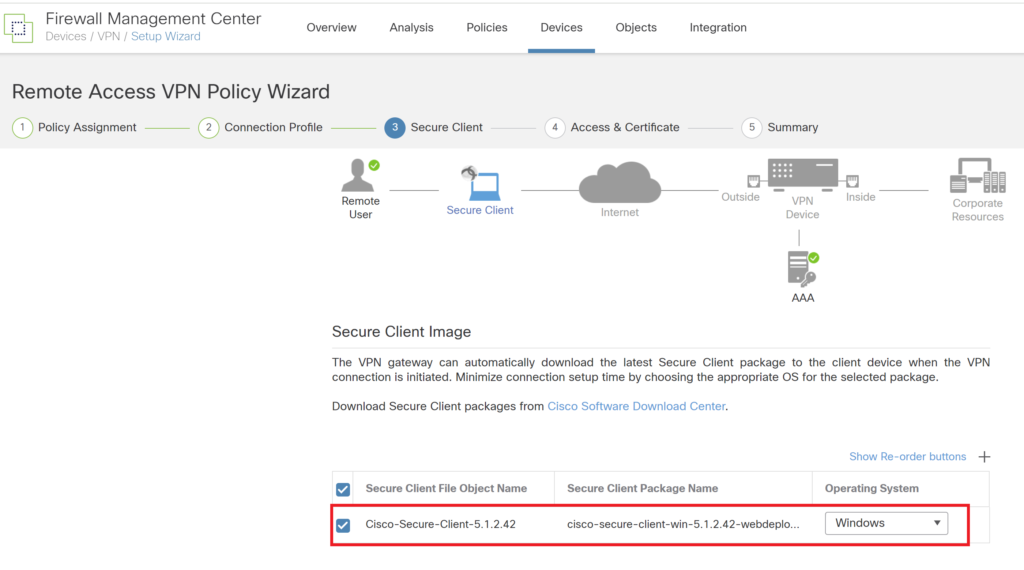
Select the zone assigned to the VPN users. Select the certificate imported in the earlier step.
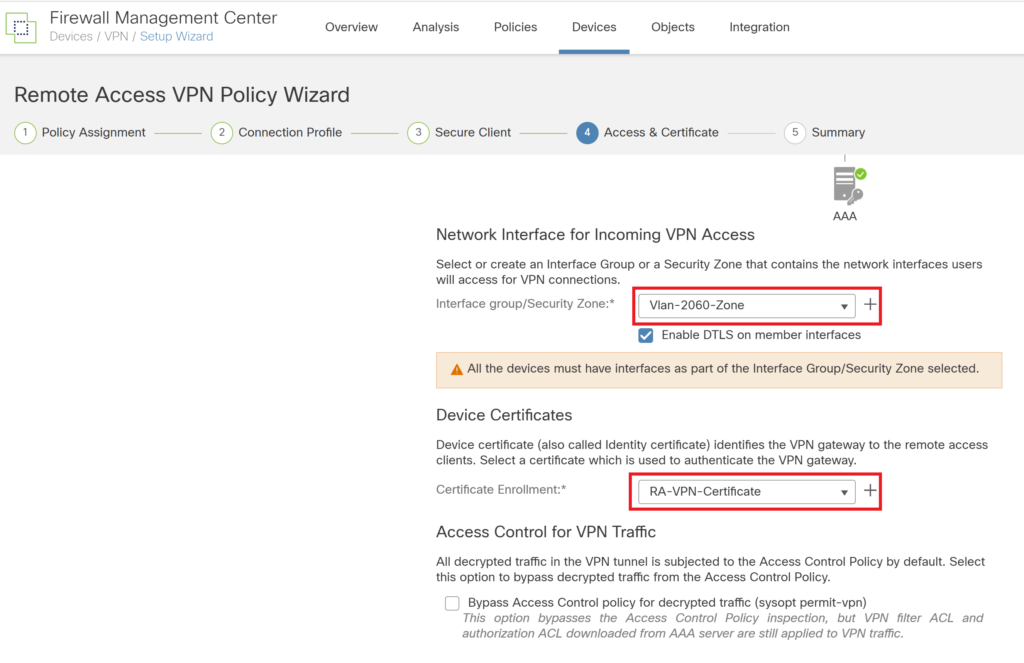
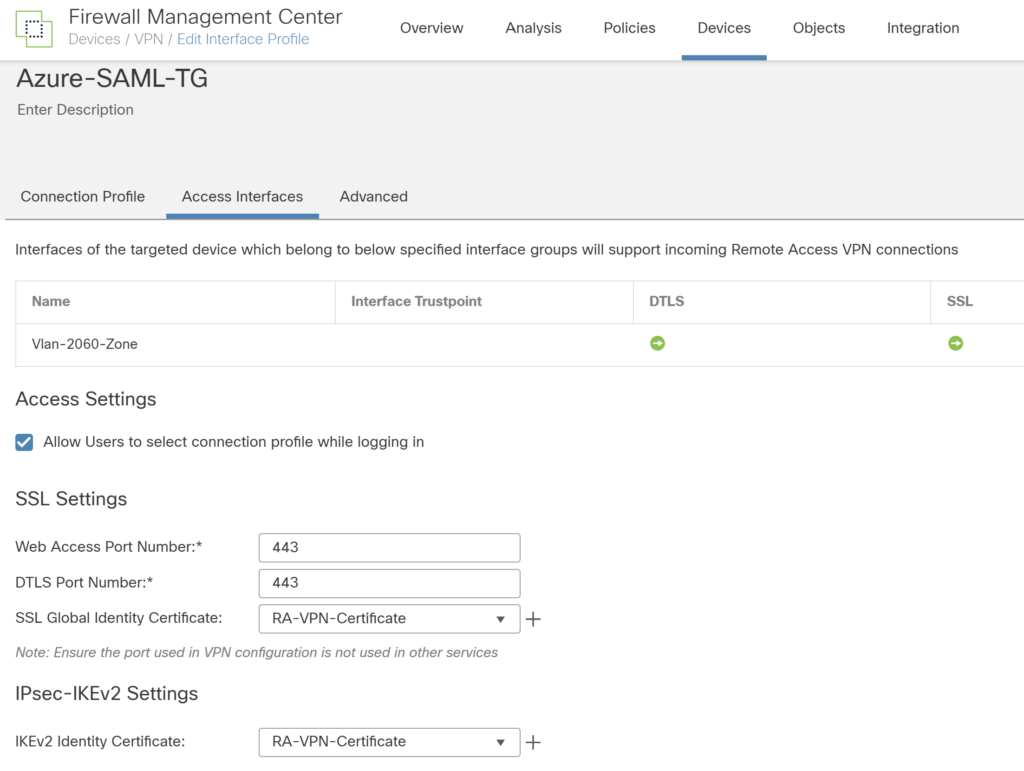
Under Access Interface Select the interface, Select the port, certificate for remote access VPN.
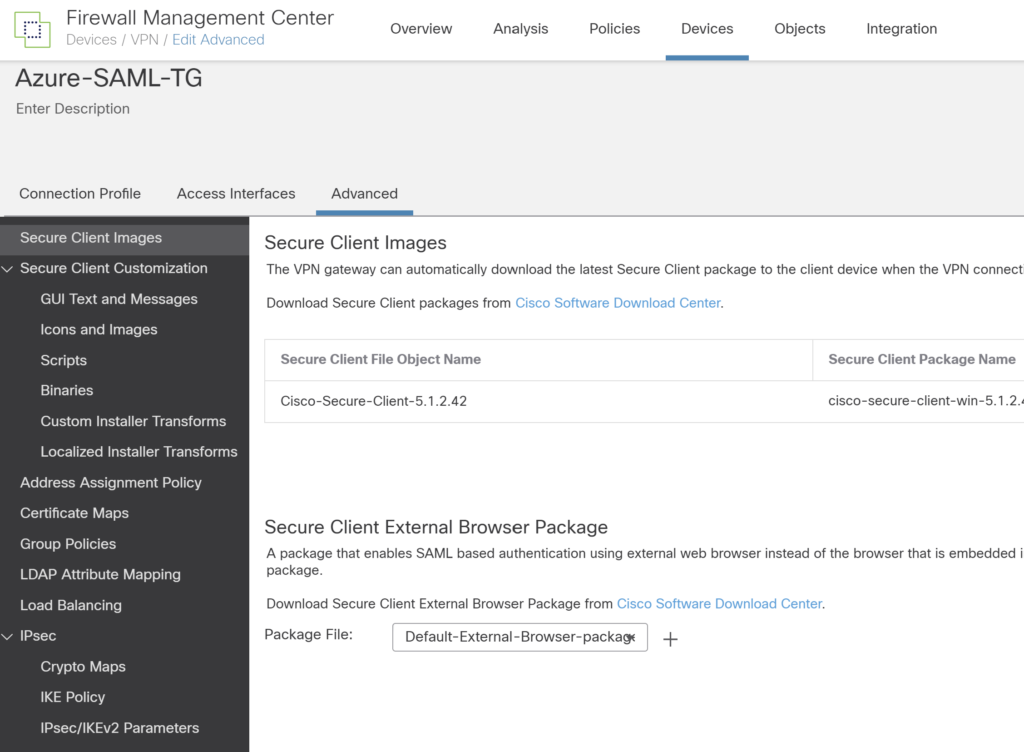
With this Cisco AnyConnect azure saml authentication configuration completes.
Note: To give access to the applications and resources we need to create access control policies and NAT rule.
Cisco FTD AnyConnect Azure SAML – Verification
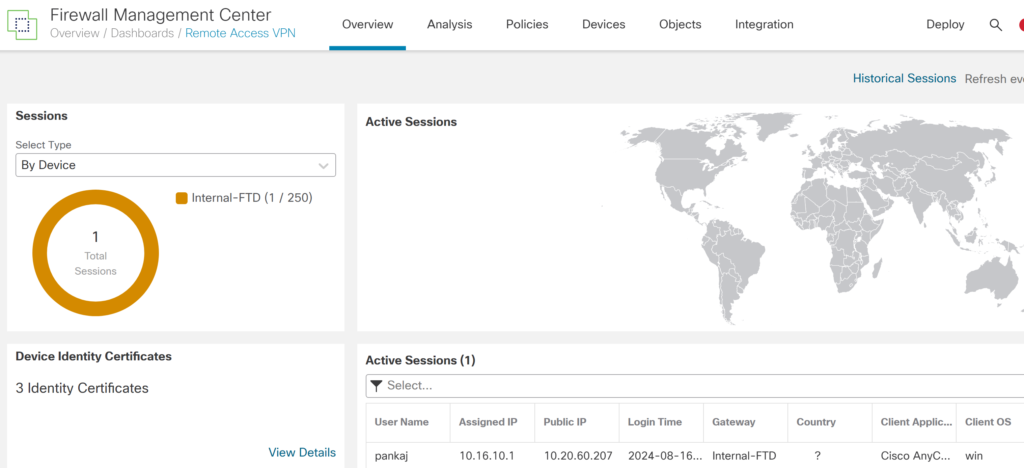
Try to connect to the VPN. The connected users can be checked on FMC remote access VPN Dashboard.
For other related post on security refer to the blog.