Since version 3.1, Cisco ISE has introduced the posture script condition. The use case for script condition is to run a script that can do complex checks that are not possible natively from ISE. The endpoint is considered compliant or non-compliant based on its exit code.
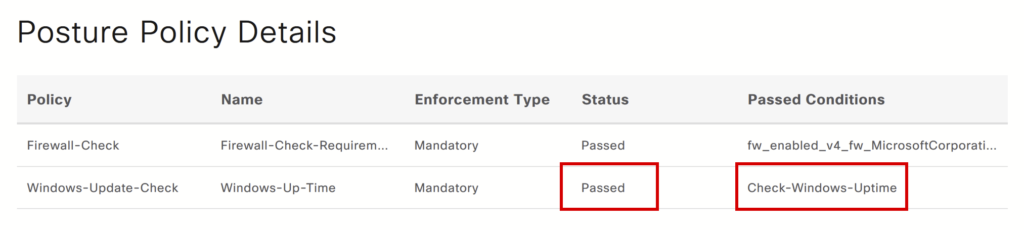
For this example, we have used Cisco ISE version 3.3. We will try to find out how long the Windows system is up. A machine with an uptime of less than four days is considered a complaint machine.
There are additional 3 steps for ISE posturing with script conditions. Refer to the previous post on the blog for the rest of the posture configuration.
Cisco ISE posture script condition – Script
For Windows, we use Powershell script. Whereas for Mac-os and Linux operating systems, we will shell script.
The script used for this post is as follows.
Note: Exit code 0 or less is considered a pass. Exit Codes greater than 0 are considered failures.
function Get-Uptime {
$os = Get-WmiObject win32_operatingsystem
$uptime = (Get-Date) - ($os.ConvertToDateTime($os.lastbootuptime))
$uptimehr=$uptime.TotalHours
if ($uptimehr/96 -lt 1){
exit 0
}
else{
exit 200
}
}
Get-UptimeCisco ISE posture script condition – Script Condition
Navigate to Policy > Policy Elements > Conditions > Posture > Script Conditions – Click Add.

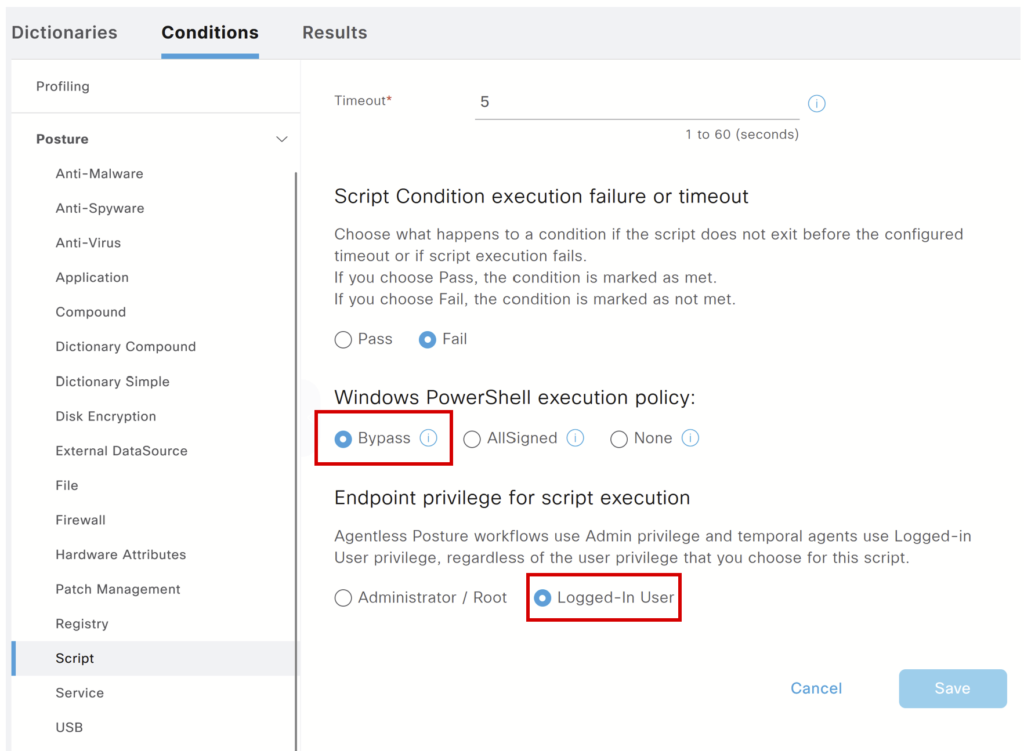
Refer to the previous post on the blog for the rest of the posture configuration.
Cisco ISE posture script condition – Endpoint Configuration
The endpoint will execute the PowerShell script.
We need to get the Cisco ISE portal certificate SHA256 fingerprint. Update the file “AnyConnectLocalPolicy.xml” in the “C:\ProgramData\Cisco\Cisco Secure Client\” folder.
Note: We can also take the sha256 fingerprint of Intermediate or root certificate.
a) Navigate to Administration > System > Certificate Management > System Certificates, Select the certificate used for the portal, and click View.
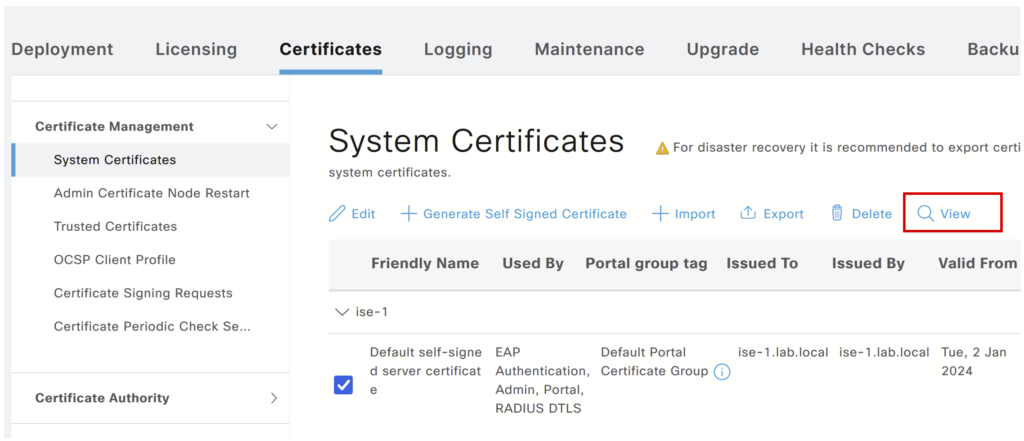
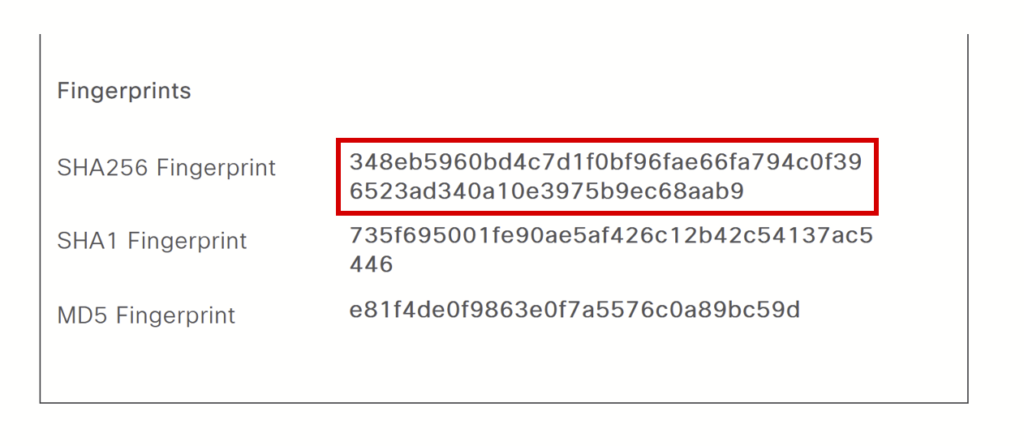
Update the file as shown in the screenshot.

<TrustedISECertFingerprints>
<fingerprint>
<algorithm>SHA-256</algorithm>
<hash>34:8E:B5:96:0B:D4:C7:D1:F0:BF:96:FA:E6:6F:A7:94:C0:F3:96:52:3A:D3:40:A1:0E:39:75:B9:EC:68:AA:B9</hash>
</fingerprint>
</TrustedISECertFingerprints>Note: We can specify multiple fingerprint tags.

Note: All steps mentioned in the document are mandatory to configure Cisco ISE posture script condition.
For additional details, refer to the ISE configuration guide on the Cisco website.