Cisco Identity Services Engine (ISE) is a powerful network security policy management platform. Integrating Cisco ISE with Security Assertion Markup Language (SAML) enhances authentication capabilities by enabling Single Sign-On (SSO). In this post, we’ll walk you through the Cisco ISE SAML integration with Duo Security to improve access security while ensuring seamless access to the sponsor portal. Using a similar approach we can configure SAML for other ISE portals.
Integration Steps
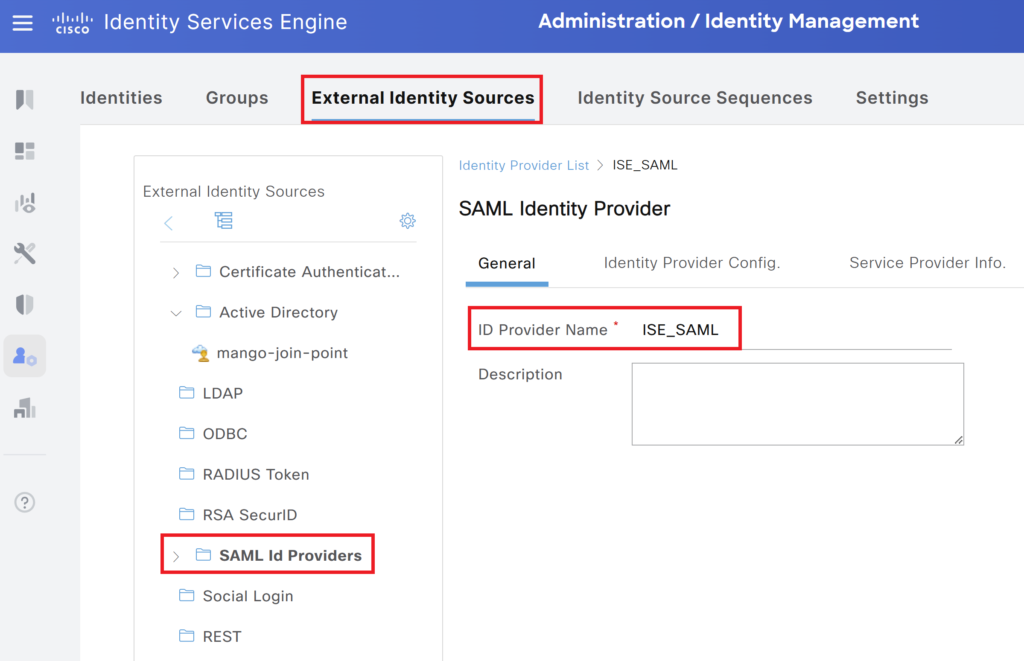
Cisco ISE SAML Integration – External Identity Sources
- Log in to the Cisco ISE Admin Console.
- Navigate to Administration > Identity Management > External Identity Sources.
- Click on Add and select SAML Identity Provider.
- Click Save, We will do the rest of the configuration in the next steps.
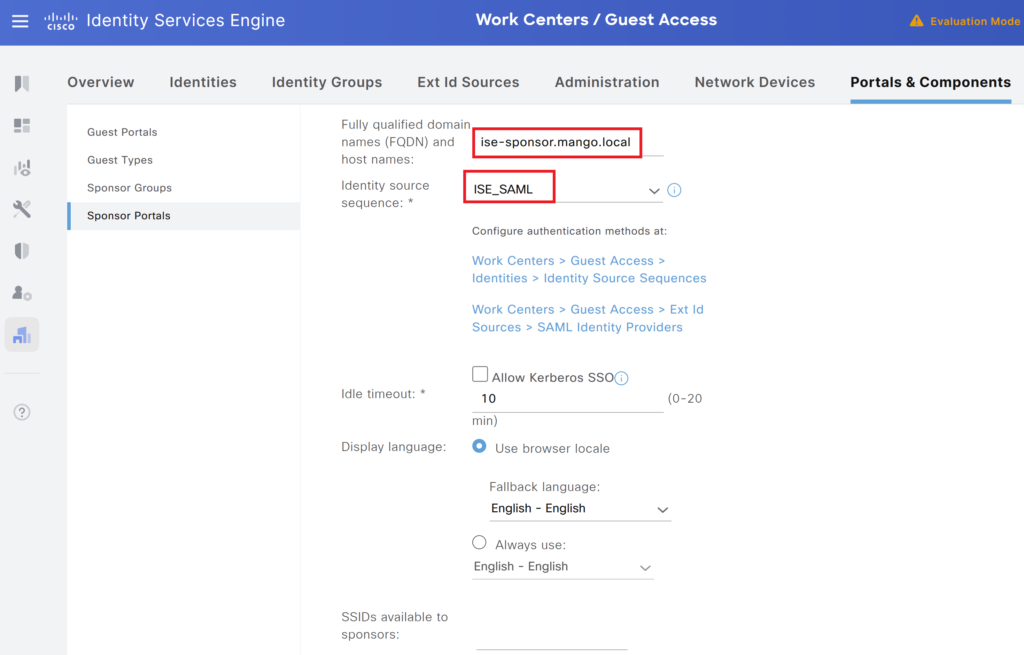
Cisco ISE SAML Integration – Sponsor Portal Configuration
- Navigate to Administration > Portals & Components > Sponsor Portals.
- Click Create New Sponsor Portal or edit an existing one.
- Change the authentication source to the External Identity source created in the previous step.
- Change the FQDN to the desired FQDN of the sponsor portal.
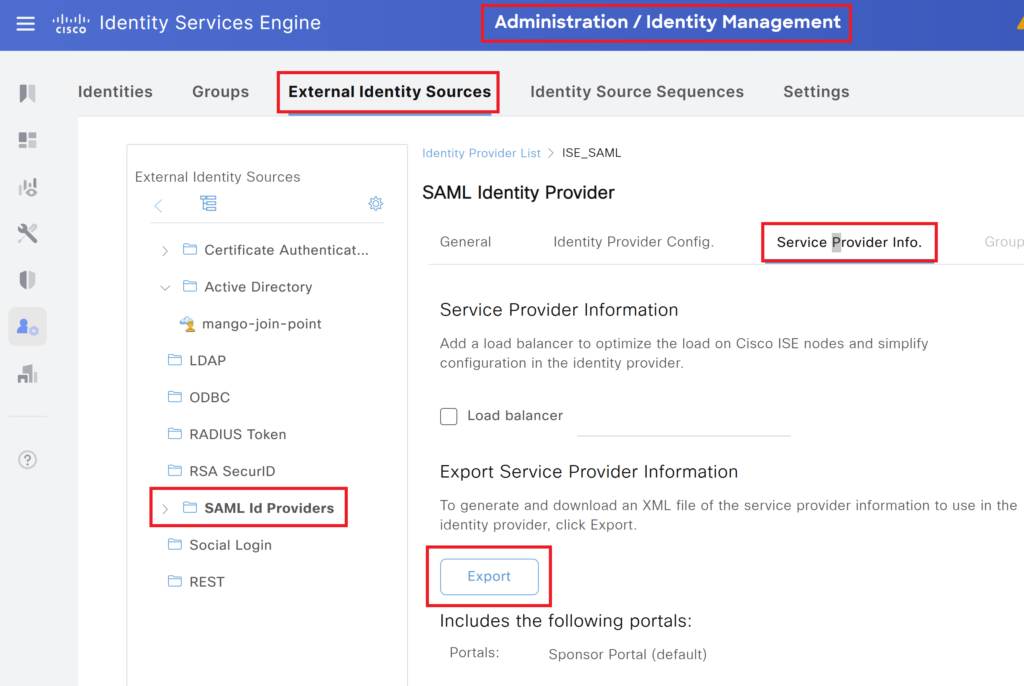
Navigate to Administration > Identity Management > External Identity Sources. Open the SAML ID provider you created in the previous step and click export.
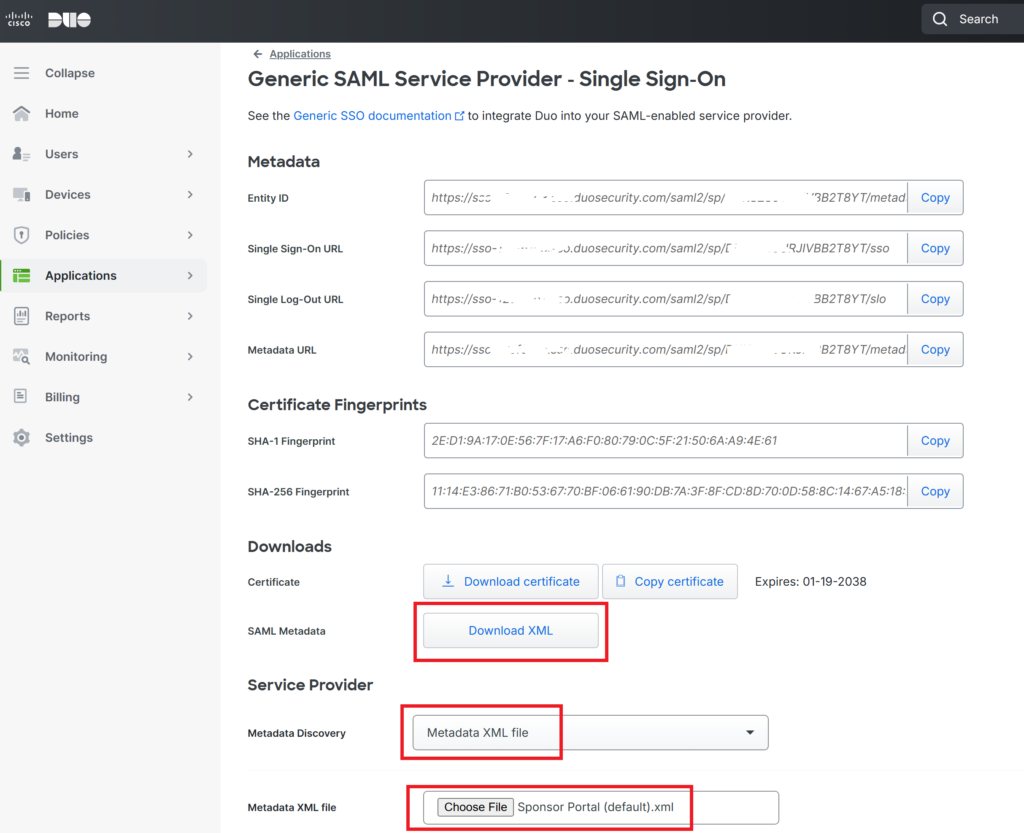
Cisco ISE SAML Integration – Cisco Duo Configuration
- Log in to the Duo Admin Panel.
- Navigate to Applications > Protect an Application.
- Select Generic SAML Service Provider.
- Download the SAML Metadata file XML file.
Important Step: The Sponsor Portal needs a group attribute sent from Duo. Using this group attribute we can
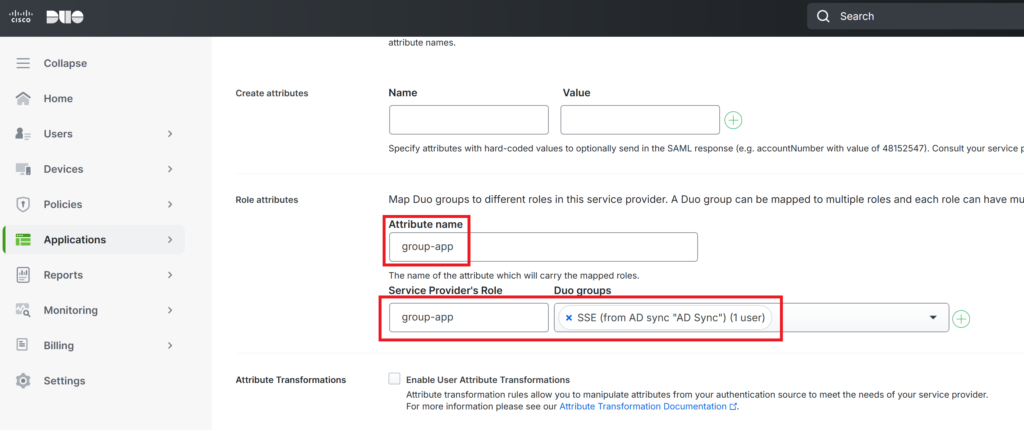
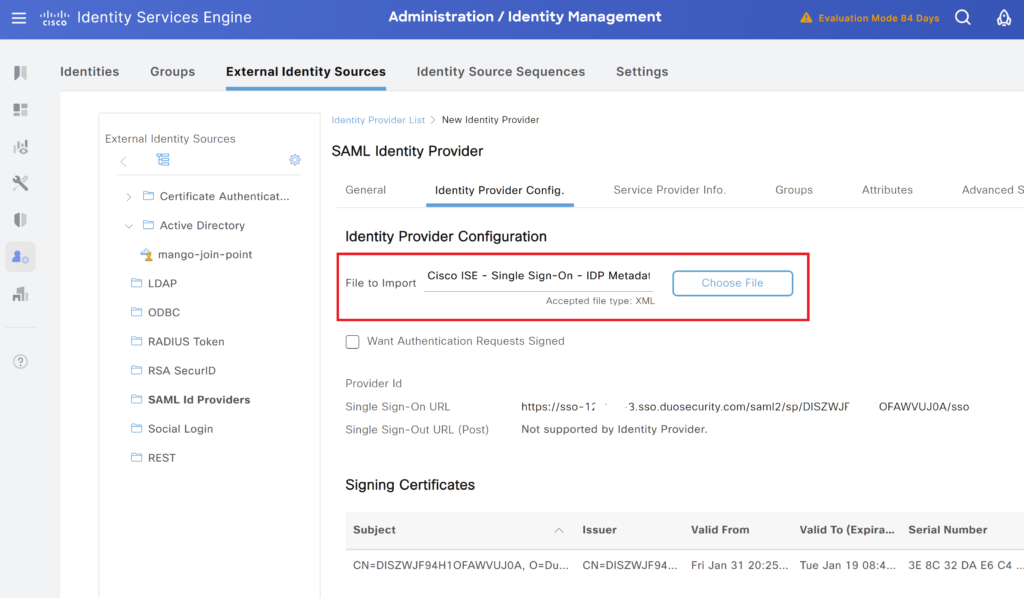
Cisco ISE SAML Integration – Import SAML metadata
Navigate to Administration > Identity Management > External Identity Sources, select the SAML Identity provider, and import the downloaded XML file.
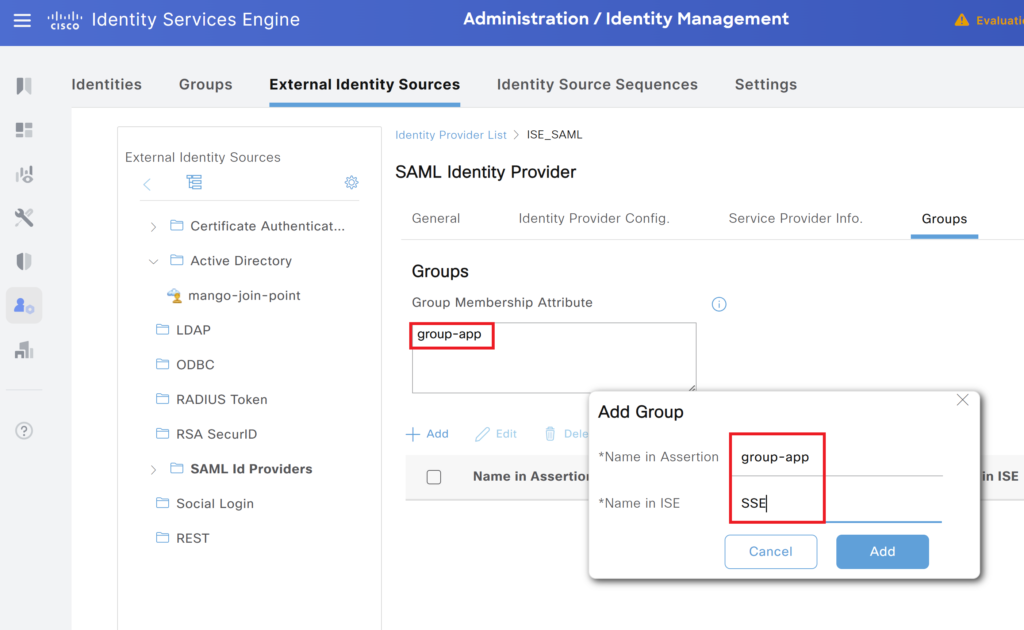
Under the group membership option enter the details of the group mentioned on the Duo Portal.
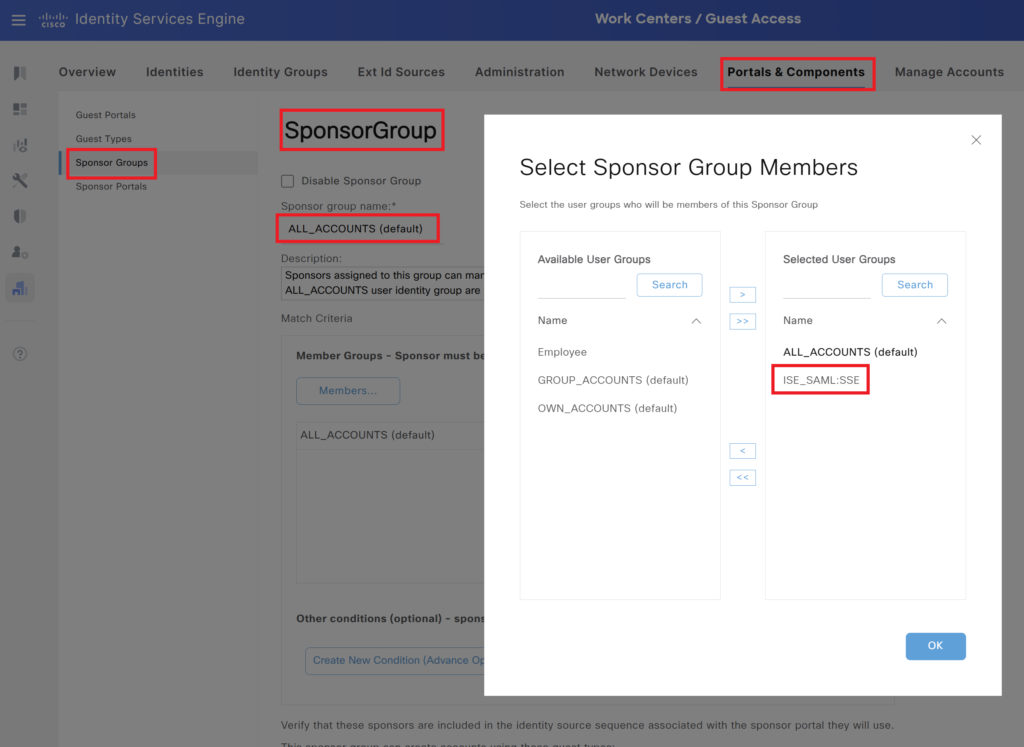
Navigate to Administration > Portals & Components > Sponsor group under the All_Accounts group and add the SAML IDP created earlier.
Cisco ISE SAML Integration – Verification
- Access the Sponsor Portal URL.
- Try logging in with a user that should authenticate via SAML.
- Verify that Duo prompts for MFA and completes authentication.
Troubleshooting Cisco ISE SAML Integration Issues
If you encounter issues, check the following:
- SAML Metadata Mismatch: Ensure that the Entity ID and ACS URL match between Cisco ISE and Duo.
- Authentication logs on Duo: Check if authentication is successful on the Duo Logs.
- Get the developer tool output to analyzethe SAML response.
- Check debug logs on ISE to check the SAML response and the group. For example, in the below logs the group is missing and due to that sponsor portal will show authentication failed.
2025-02-01 10:19:10,020 DEBUG [https-jsse-nio-10.20.60.8-8445-exec-8][[]] cpm.saml.framework.impl.SAMLFacadeImpl -:::::- AuthenticatePortalUser – added user groups from SAML response to AuthenticationResult, all retrieved groups:[]
Debugging Cisco ISE SAML Integration Issues
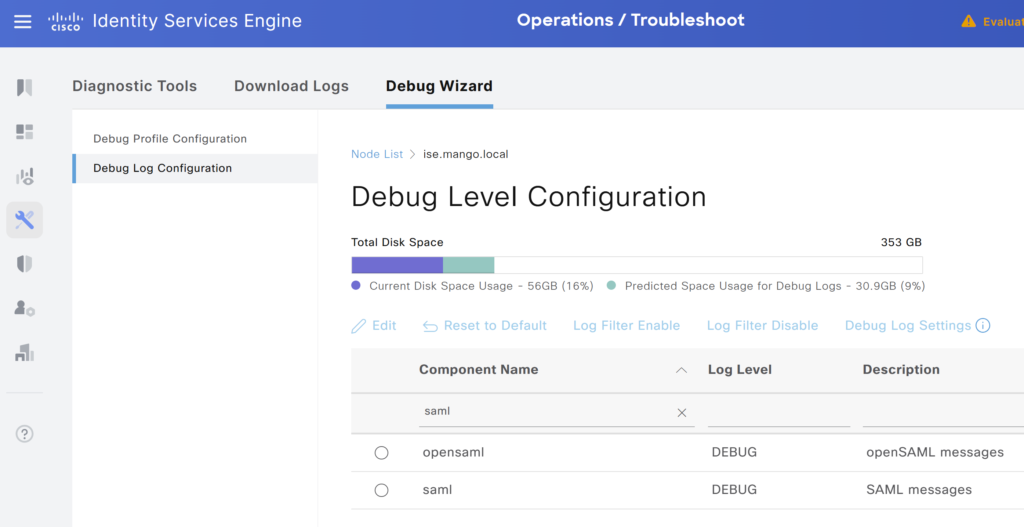
- Navigate to Operations > Troubleshoot > Debug Wizard.
- Select SAML Authentication and set the logging level to DEBUG.
- Check logs in the ise-psc.log file. The live debug logs can be viewed on CLI of the node using the command “show logging application ise-psc.log tail“
The integration steps will remain similar for any IDP like Entra ID. Refer to the official admin guide of Cisco ISE for further details.
Feel free to put your comments below for any suggestions on the post.