We will walk through the step-by-step configuration of GPO certificate auto enrollment. The GPO will push a unique certificate on a domain-joined machine. The certificates can be pushed to the user’s or machine’s account for use in 802.1x authentication, allowing for efficient authentication in wired and wireless environments. With automatic enrollment, an administrator can roll out certificates on a large scale. For 801.x authentication configuration refer to earlier post. For further details on GPO refer to Microsoft website.
GPO Certificate Auto Enrollment – Certificate Authority Setup
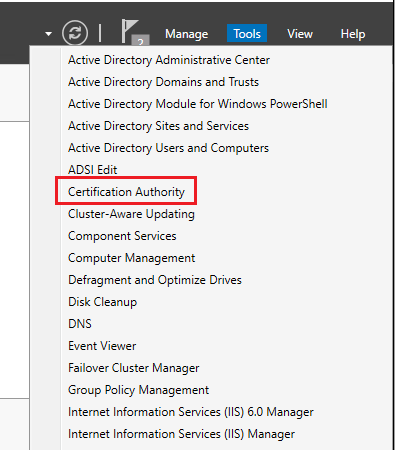
Step 1> Open Certification Authority. Open the server manager, click on Tools, and select Certification Authority.
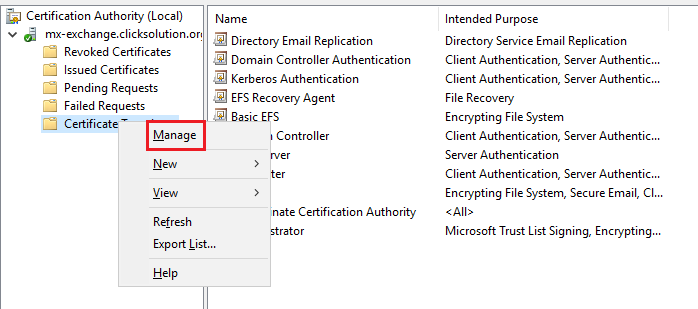
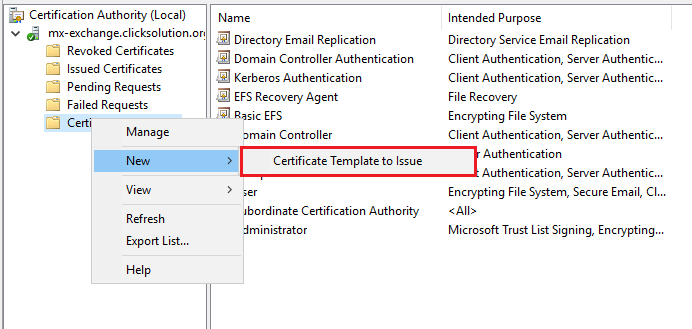
Step 2> Create a new template. Right-click on Certificate templates and select manage.
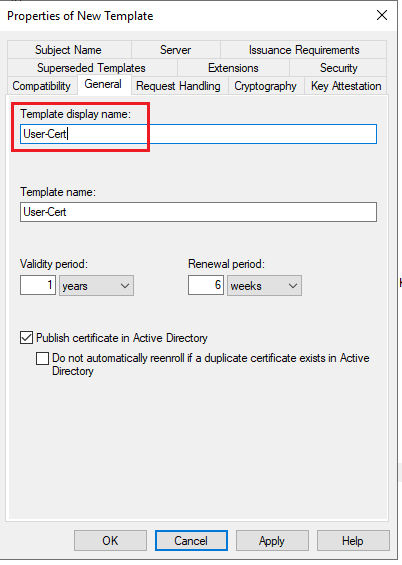
There is a default template for the user, right-click and duplicate.
Edit the details of the duplicated template.
Give permissions (Read, Enroll, Autoenroll) to the required group.
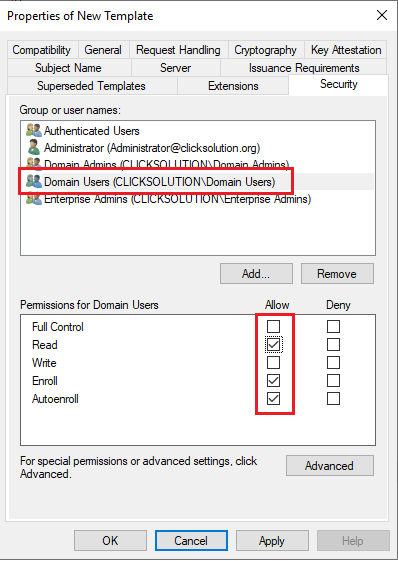
Add the newly created template to the Certificate templates:
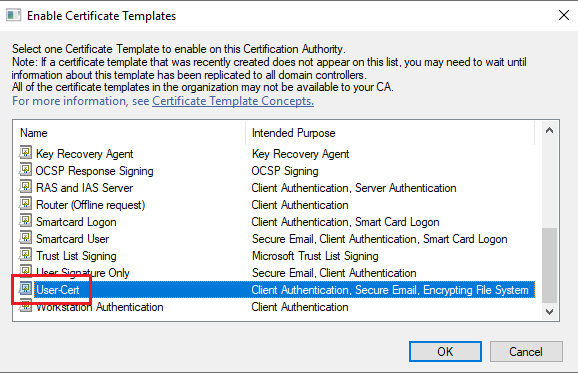
Select the created template and click ok.
GPO Certificate Auto Enrollment – Group Policy Configuration
We will create a group policy to enable auto-enrollment.
The list will show the configured GPO policy. For this example, we will use the “Default Domain Policy”. We can choose another policy based on the configuration.
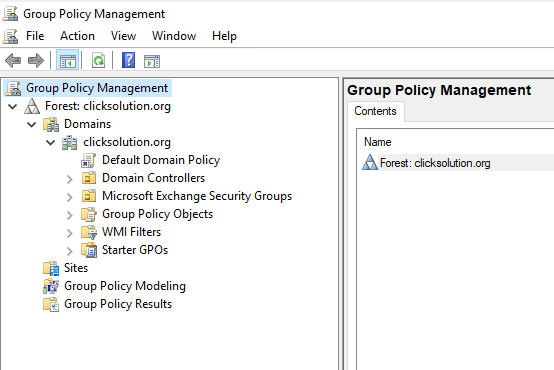
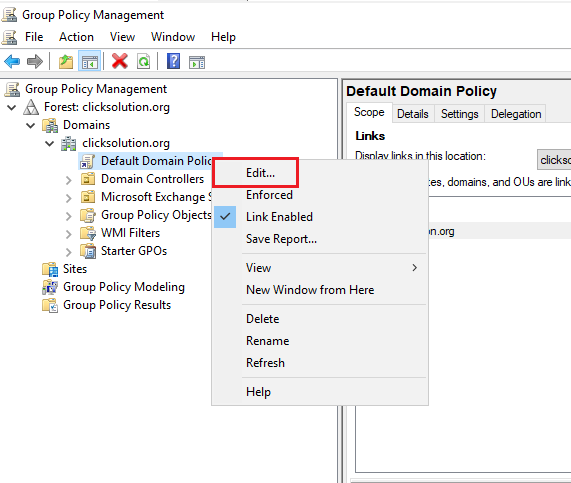
Right-click on Default domain policy and select Edit.
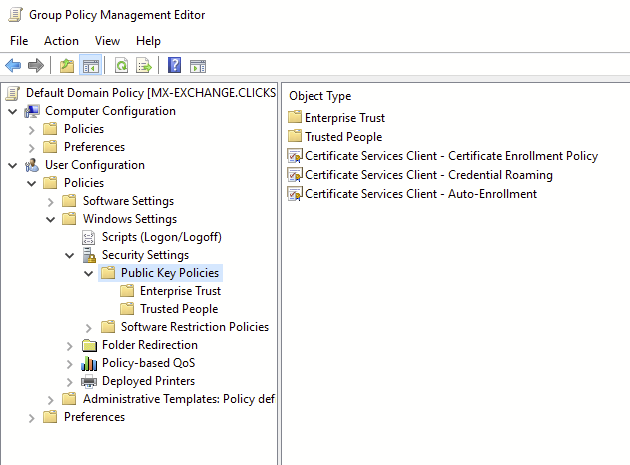
For this post, we will edit the settings for users. Expand User configuration > Windows settings> Security Settings > Public Key Policies > Right click select properties of Certificate Services Client – Auto-Enrollment
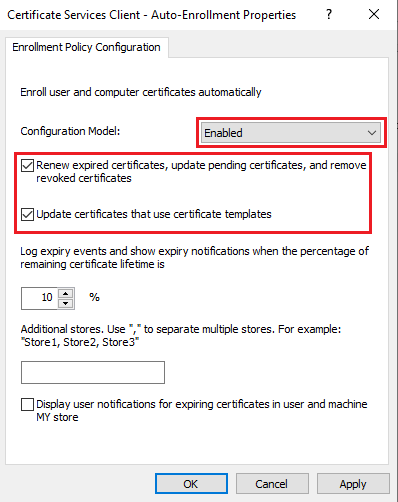
Note: The same steps we need to follow for Machine certificates.
GPO Certificate Auto Enrollment – Verification
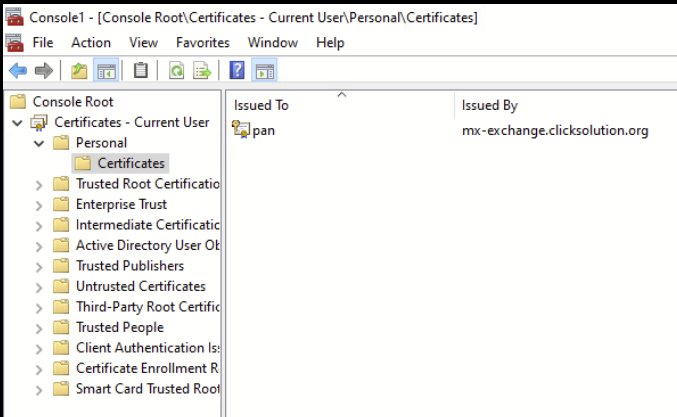
Validate user certificate in the domain machine.
Step 1> Go to run and type mmc hit enter:
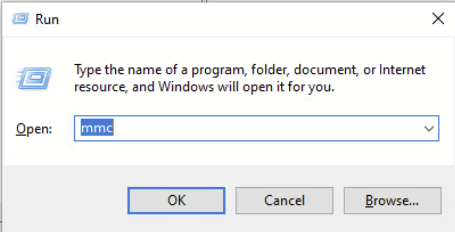
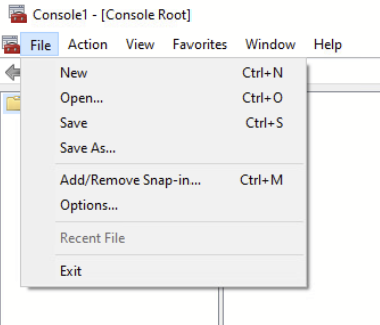
Step 2> Click on the file and Select Add/Remove Snap-in.
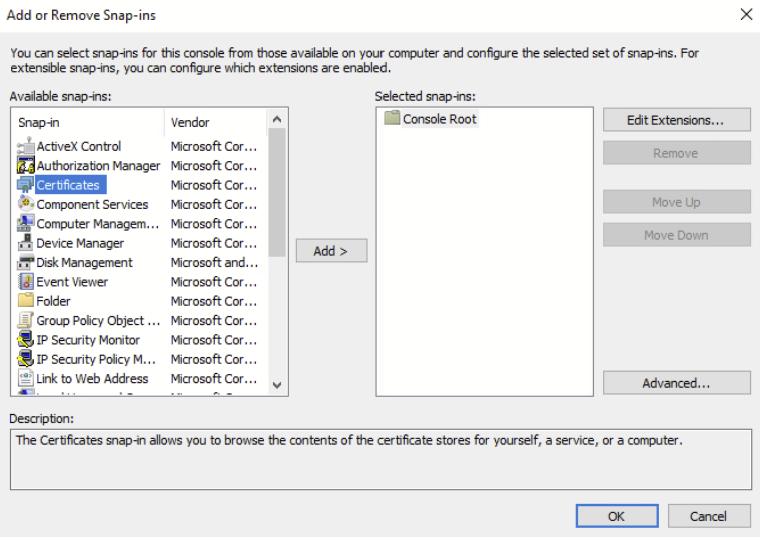
Select Certificate and click Add, then click ok.
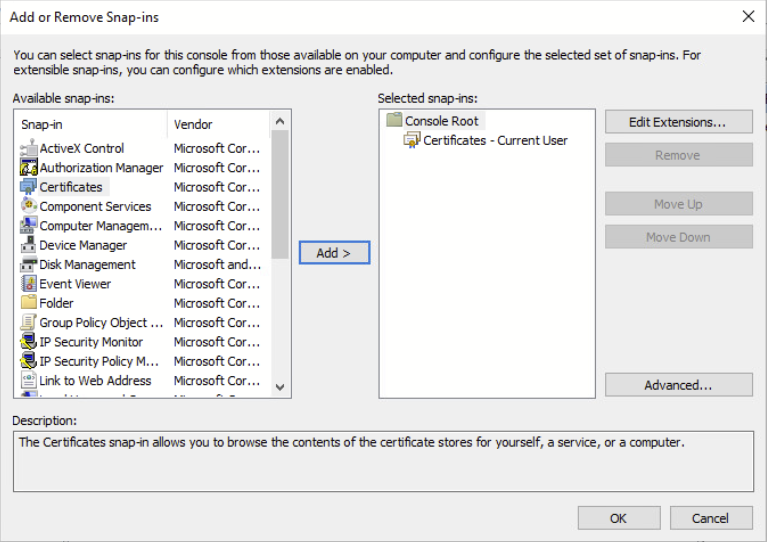
Expand the certificates for current users> Navigate to Personal > Certificates. In the below screenshot we can see there is one certificate present on the end user.